

Over the last month, Barracuda threat analysts identified several notable email-based threats targeting organizations around the world, including:
- Extortion attempts impersonating Clop ransomware
- New attacks by the evasive and highly adaptive LogoKit phishing platform
- A phishing campaign leveraging SVG image file attachments
Attackers impersonate Clop ransomware to extort payment
Threat snapshot
Why go to the trouble and expense of launching a real ransomware attack when you can just pretend to do so instead?
Barracuda’s threat analysts recently uncovered an email attack where the scammers tried to convince targets that they were Clop ransomware and had successfully breached the company network and stolen sensitive data. The attackers threatened to expose the information unless the victim paid an unspecified sum.
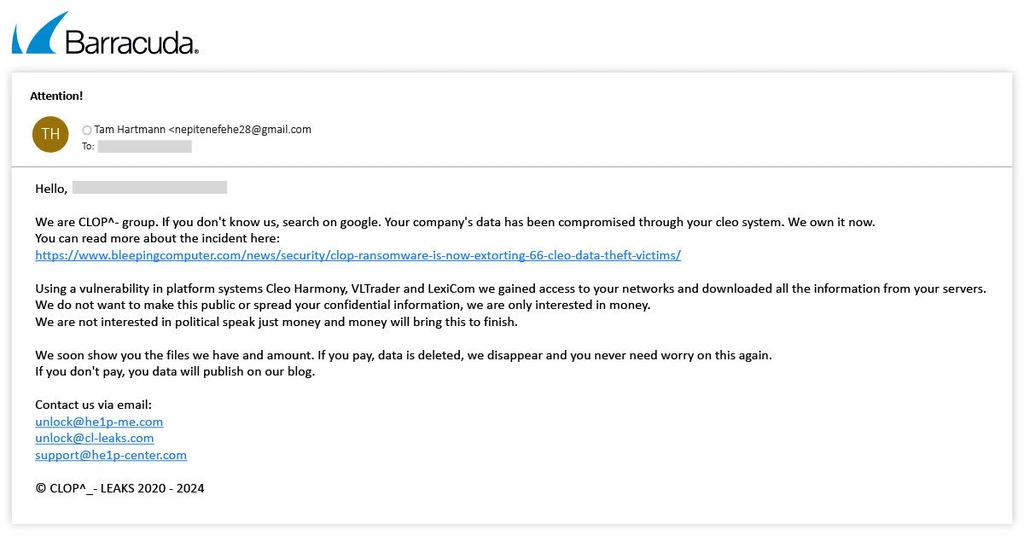
In their extortion email, the attackers claimed to have exploited a vulnerability in Cleo, the developer behind a range of managed file transfer platforms, including Cleo Harmony, VLTrader, and LexiCom. This attack method is widely associated with Clop ransomware.
The attackers claimed they had secured unauthorized access to the victim’s company network and had downloaded and exfiltrated data from servers. To lend authenticity to their claims, they pointed the target to a media blog post reporting on how Clop had stolen data from 66 Cleo customers using this approach.
The attackers provided a series of contact email addresses and urged the victim to get in touch.
Signs to look for
- Emails from the fake Clop are likely to reference media coverage about actual Clop ransomware attacks.
- If the email features elements such as a 48-hour payment deadline, links to a secure chat channel for ransom payment negotiations, and partial names of companies whose data was breached, then you are likely dealing with actual Clop ransomware, and you need to take immediate steps to mitigate the incident.
- If these elements are absent, you’re probably just being scammed.
LogoKit phishing kit evades detection with unique links and real-time victim interaction
Threat snapshot
Barracuda analysts encountered the well-established LogoKit phishing-as-a-service platform distributing malicious emails claiming to be about urgent password resets.
LogoKit has been active since 2022, and its features and functionality help it evade traditional security defenses and make detection and mitigation significantly more difficult.
LogoKit, among other things, has the alarming capability of real-time interaction with victims. This means that attackers can adapt their phishing pages dynamically as the victim types in their credentials. LogoKit retrieves the company logo from a third-party service, such as Clearbit or Google’s favicon database.
LogoKit is very versatile. It integrates with popular messaging services, social media, and email platforms to distribute its phishing. It can generate unique phishing pages for each target. This level of versatility also makes detection harder for traditional security defenses.
In the most recent campaign seen by Barracuda threat analysts, the attackers distributed authentic-looking emails with the headers of “Password Reset Requested” or “Immediate Account Action Required.”
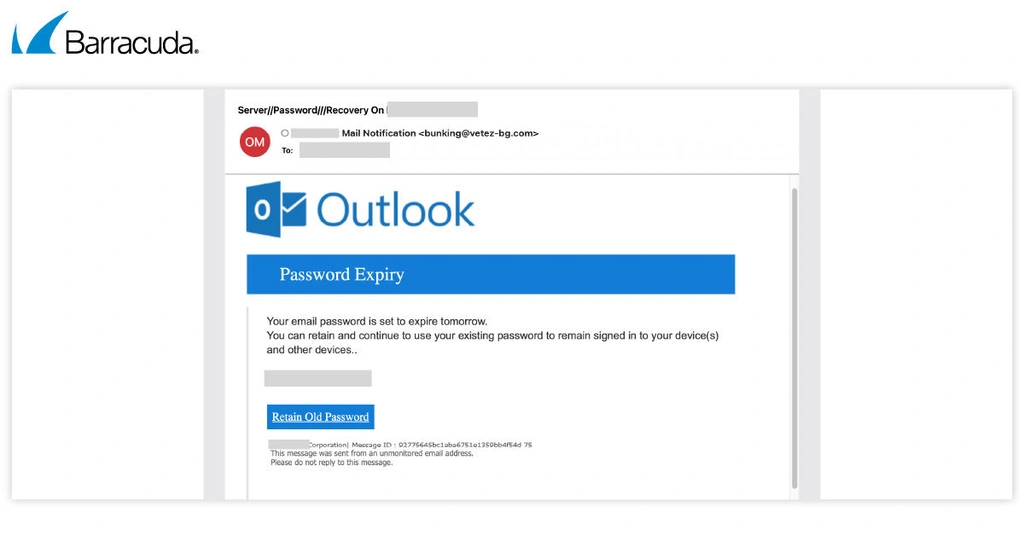
These headers create a sense of concern and urgency, designed to encourage the recipient to quickly click on the link to resolve the supposed issue. Instead, they are redirected to a dynamically created phishing page hosted by LogoKit.
This page is designed to look identical to the login portal and password reset page of the service the victim believes they are connecting to. The victim is prompted to enter their login credentials, which are then captured by the attacker.
Signs to look for
- The URL pattern to look for:
- https://ExampleURL.#.[ key + Victim’s Email ]
- https://ExampleURL/[ key + Victim’s Email ]
- https://ExampleURL.#.[ base64 encoded url + Victim’s Email ]
Pattern of the hyperlink to Clearbit and Favicon to fetch the logo:
- <img src=”https://logo.clearbit.com/Victim domain” >
- <img src= “https://www.google.com/s2/favicons?domain=Victim domain” >
Phishing attacks exploiting SVG graphic attachments
The use of malicious attachments in phishing attacks, with minimal or no text in the email body, is rising. Threat analysts have seen attacks using PDFs, HTML, HTM, Word documents, Excel files, and ZIP archives.
As detection tools improve, attackers continue to adapt their attack methods, and Barracuda threat analysts have recently noted a shift toward using SVG (Scalable Vector Graphics) attachments in phishing attacks. Some of these attacks are delivered using popular phishing-as-a-service (PhaaS) platforms, such as Tycoon 2FA.
SVG is a type of image format that is ideal for websites because the images can be made larger or smaller without losing resolution quality. SVG files are generally written in web-friendly XML.
According to Barracuda’s analysts, SVG files are becoming a popular method for delivering malicious payloads due to their ability to contain embedded scripts, which don’t look suspicious to security tools.
In the samples analyzed by Barracuda, the attacks are of the traditional “urgent fund transfer” variety or designed to steal Microsoft credentials. In more complex attacks, opening the email attachment triggers the download of a malicious ZIP file.
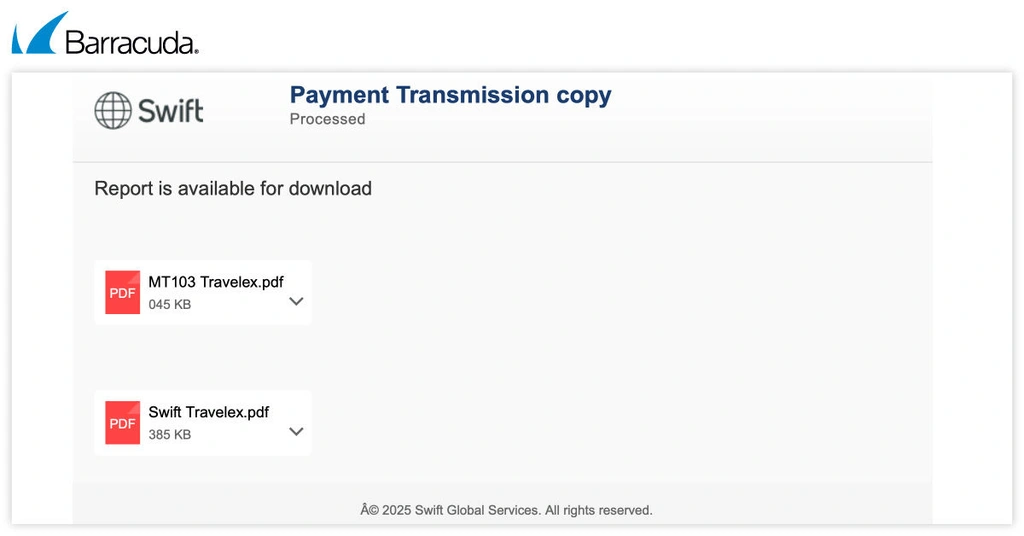
If a sandbox environment is detected, the attackers redirect the “victim” to a popular legitimate shopping website instead.
Signs to look for
- If an email has an .SVG attachment with clickable links, avoid interacting with the attachment.
- Other red flags include SVG files prompting the download of additional files and the appearance of browser warnings or security alerts when opening the file.
How Barracuda Email Protection can help your organization
Barracuda Email Protection offers a comprehensive suite of features designed to defend against advanced email threats.
It includes capabilities such as Email Gateway Defense, which protects against phishing and malware, and Impersonation Protection, which safeguards against social engineering attacks.
Additionally, it provides Incident Response and Domain Fraud Protection to mitigate risks associated with compromised accounts and fraudulent domains. The service also includes Cloud-to-Cloud Backup and Security Awareness Training to enhance overall email security posture
Barracuda combines artificial intelligence and deep integration with Microsoft 365 to provide a comprehensive cloud-based solution that guards against potentially devastating, hyper-targeted phishing and impersonation attacks.
This article was originally published at Barracuda Blog.
Photo: instaphotos / Shutterstock


what a great info packed posting, passing it on to a few people for awareness.
thanks
Phishing and ransomware attacks are happening ever more frequently and are getting ever more sophisticated. We need proper, performant and up-to-date tools to combat these threats, but users need to be educated to stay vigilant at all times.
Well-written and eye-opening article! Cyber threats are evolving rapidly, and organizations must stay vigilant. Implementing strong email security measures and continuous user awareness training is essential to defending against these increasingly sophisticated attacks.
Very helpful, thank you
This article does a great job highlighting the latest email threats. The part about extortion scams pretending to be Clop ransomware and the tricky LogoKit phishing tactics really stood out. It’s a good reminder that cybercriminals are always finding new ways to bypass defenses, and staying on top of email security is more important than ever.
I must say, having not seen this tactic before, impersonating a known ransomware group is quite creative. I am sure that many uneducated, unprotected c-level folks would panic and click anything/everything in the email. I’ll opine that the link to Bleeping Computer could have also not been the true URL but instead redirected to a data capture site that mimicked MSFT or something else official.
Great share from Barracuda!
Always enjoy a more detailed look. very helpful