Results for: tech time warp

Tech Time Warp: Even UNIVAC was susceptible to viruses
It’s easy to think about viruses as a product of the PC era. But, one of the first viruses ever created affected UNIVAC computers. Although ANIMAL was ultimately a benign creation—a game spread by a separate program called PERVADE—its creator...

Tech Time Warp: U.S. Census Bureau signs UNIVAC contract
With the next census just two years away—it takes place April 1, 2020—it’s worth remembering the machine that computerized the U.S. Census Bureau’s operations. The bureau signed a contract on March 31, 1951, to use the UNIVAC, or the UNIVersal...

Tech Time Warp: Edmund Berkeley, a giant brain of computing
Computer history is filled with quirky individuals—and Edmund Berkeley, born March 21, 1909, is among the most fascinating. It’s hard to pinpoint what Berkeley should be most known for: Founding the Association for Computing Machinery (ACM)? (Relations with ACM later...

Tech Time Warp: Homebrew Computer Club Meets in a Garage
Never underestimate a group of guys who want to hang out in the garage. After all, the Homebrew Computer Club began meeting In programmer Gordon French’s Menlo Park, California, garage in March 1975 — and while the neighbors might have...

Tech Time Warp: A Look Back at the Ping-Pong Virus
Thirty years ago, a little bouncing ball was driving computer users bonkers. Discovered at Italy’s University of Turin in March 1988, the Ping-Pong virus was a boot sector virus affecting MS-DOS machines. It spread via infected floppy disks. (Remember those?)...

Tech Time Warp: A Language That’s Anything But, Well, Basic
Basic is such a loaded term these days. The kids use it as a synonym for unremarkable and uninteresting—interestingly enough, words that could not describe BASIC, the computer language co-invented by John Kemeny and Thomas E. Kurtz at Dartmouth University.
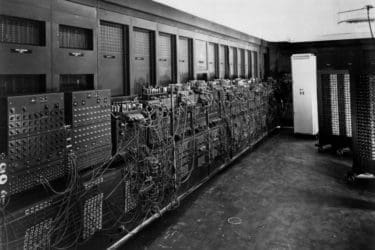
Tech Time Warp: Meet ENIAC, the First Digital General Purpose Computer
It might lack the immediate name recognition of Harvard’s Mark I or Bletchley Park’s Colossus, but the University of Pennsylvania’s ENIAC stands right next to them in the annals of computer history. The Electronic Numerical Integrator and Computer made its...

Tech Time Warp: Garry Kasparov’s Rage Against the Machine
The precarious relationship between man and machine has always preoccupied the technologically minded. Computer genius Alan Turing was asking “Can machines think?” as early as 1950. Few of us, though, have devoted as much time to the question—or been as...

Tech Time Warp: First published reference to vaporware
In Texas, they call it “all hat, no cattle.” In Silicon Valley, they call it vaporware, and the first use of the term was in a Feb. 3, 1986, Time Magazine article by Philip Elmer-DeWitt about the delayed release of...

Tech Time Warp: Happy birthday to Douglas Engelbart, inventor of the mouse
Born Jan. 30, 1925, Douglas Engelbart isn’t a household name for most people, but we all know—and many of us can’t live without—his most famous invention: the computer mouse. The Portland, Oregon, native served as a Navy radar technician in...
