 These days, every MSP is well aware of the risks of ransomware (and hopefully using cloud backup to protect against it). But back in September 2013, the concept of malware that encrypted your files and demanded payment within a 72-hour period was new to most and alarming to all.
These days, every MSP is well aware of the risks of ransomware (and hopefully using cloud backup to protect against it). But back in September 2013, the concept of malware that encrypted your files and demanded payment within a 72-hour period was new to most and alarming to all.
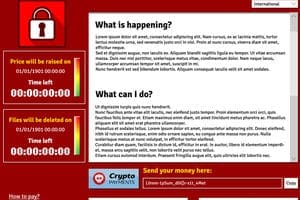
CryptoLocker made its debut in September 2013 and all told affected about 500,000 victims. The ransomware, like most forms of malware, exploited social engineering: An email arrives with an attachment appearing to be a PDF, with an urgent subject line (info about a FedEx shipment, a scan from a Xerox machine, or even a complaint about customer service). However, thanks to Windows’ hidden extension feature, the “PDF” was actually an executable attachment. Once opened, CryptoLocker encrypted the user’s files and demanded a payment (generally $300) made in Bitcoin within 72 hours. Nasty stuff.
The fallout from CryptoLocker
It’s believed the Russian gang behind CryptoLocker collected about $3 million in ransom before authorities caught up with them. By August 2014, ringleader Evgeniy Bogachev had been identified, and security experts had created an online portal where CryptoLocker victims could obtain the decryption keys they needed for free. (Bogachev is still on the loose.)
In the years since, CryptoLocker has spawned a multitude of offshoots and copycats, capitalizing on media coverage of ransomware. One spam campaign purported to offer a decryption tool but was actually spreading another form of malware, and new variants of ransomware pop up all of the time. Most businesses have learned that it’s best to plan ahead and ensure the latest versions of your files are backed up in the cloud—otherwise, better include a “ransom” line item in your IT budget. It’s not a matter of if but when ransomware tries to infiltrate your system.
Photo: Nicescene/Shutterstock; Swill Klitch/Shutterstock
