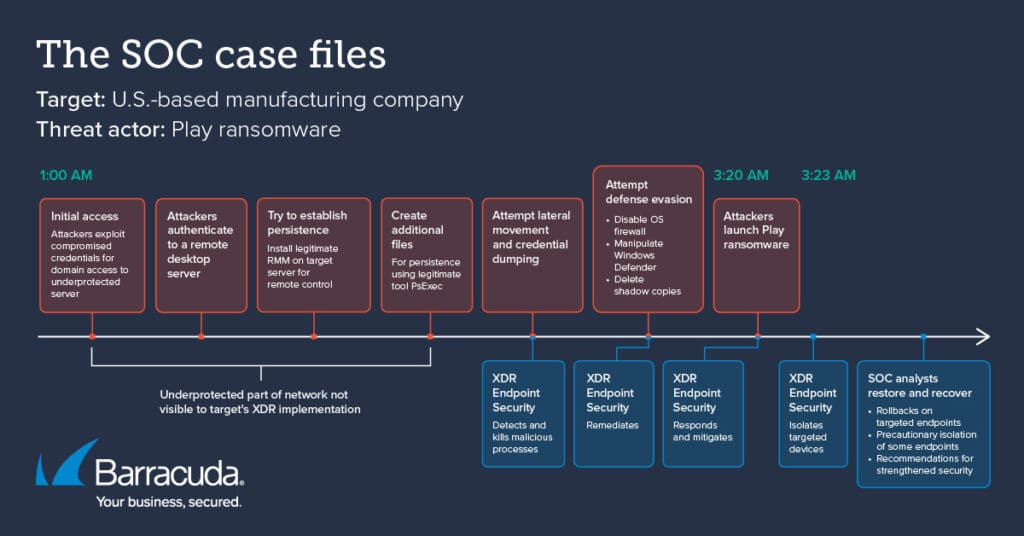
Incident summary
- A U.S.-based manufacturing company was recently targeted by the Play ransomware group in the early hours of the morning.
- The attackers broke into an under-protected domain controller at 1:00 am.
- At 3:20 a.m. the gang attempted to execute the ransomware. They targeted multiple endpoints, which the security operations center (SOC) monitored.
- The SOC identified the attack, alerted the customer, and took automated response actions.
- By 3:23 a.m., the security team blocked the attackers and locked them out of the network.
The SOC is part of Barracuda Managed XDR, an extended visibility, detection, and response (XDR) service that provides customers with round-the-clock human and AI-led threat detection, analysis, and mitigation services to protect against complex threats.
How the attack unfolded
The attack took place on a Tuesday night in October
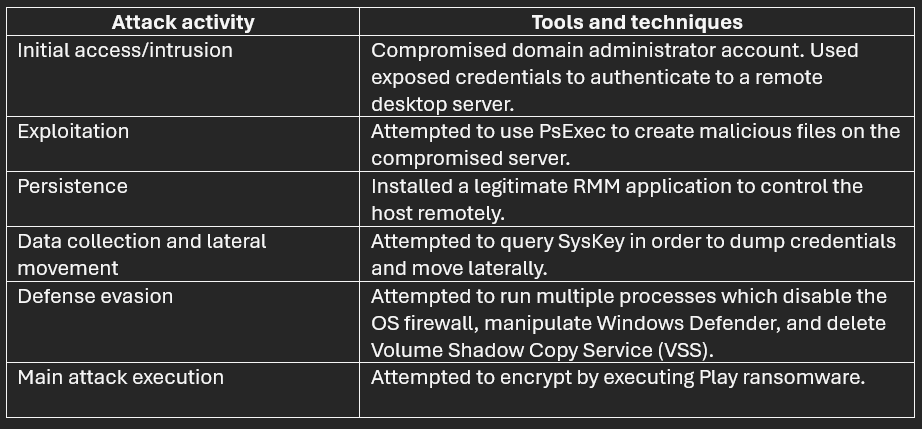
- At approximately 1:00 a.m. the sophisticated threat actors began their attack. They started by exploiting compromised credentials for a domain admin account, which allowed them to authenticate to an under-protected remote desktop server from where they planned to conduct the whole operation.
- The target did not have XDR server security in place, leaving a gap in monitoring capabilities that could have detected anomalous activity on the domain controller at the very start of the attack.
The main attack
- The attackers then tried to establish persistence. They did so by installing a legitimate remote monitoring and management (RMM) application on the target server so that they could control the host remotely.
- Next, the attackers employed a living off the land (LOLT) tactic by using PsExec, a native Windows tool commonly abused by threat actors. The group used PsExec to create additional files to maintain persistence.
- The attackers then attempted to query the registry to obtain the SysKey to conduct credential dumping and lateral movement. XDR Endpoint Security detected the activity and successfully killed the malicious process.
- After this, the attackers attempted to evade defenses by disabling the OS firewall, manipulating Windows Defender, and attempting to delete shadow copies — all of which were also remediated by XDR Endpoint Security.
- Finally, at 3:20 a.m. the attackers attempted to execute Play ransomware to encrypt several assets. XDR Endpoint Security quickly mitigated the ransomware.
- By 3:23 a.m. the targeted endpoints were isolated from the network, and the attack had failed.
Restore and recover
- XDR Endpoint Security’s SentinelOne agent killed, quarantined, and mitigated the malicious processes and files throughout the attack lifecycle.
- The Storyline Active Response (STAR) custom rules developed by Barracuda’s SOC engineers effectively detected the file manipulation that signaled attempted encryption and took response actions to isolate the targeted endpoints.
- Barracuda’s SOC analysts, who operate 24×7, sprang into action to isolate as a precaution any additional endpoints where suspicious activity was observed.
- The SOC also issued rollback commands to restore the targeted endpoints to their prior state, before the threats were present.
- The SOC analyzed the events, established a timeline, and identified key artifacts, including the compromised admin account, breached server, and communication with a malicious IP.
- The SOC provided critical recommendations to the organization to help them strengthen the security of their environment.
The main tools and techniques used in the attack
Lessons learned
Cyberattacks often originate across multiple layers and the most comprehensive protection is provided by extended visibility and layered defenses.
Due to a lack of security cover, the attackers could remain invisible in the early stages of the attack and exploit a domain controller for privilege escalation and lateral movement—a common tactic in sophisticated attacks. The attackers remained active in the network for over two hours before reaching an XDR-monitored endpoint, where the team mitigated and remediated the attack within minutes.
Barracuda XDR features like Threat Intelligence, Automated Threat Response and the integration of wider solutions such as XDR Server Security, XDR Network Security, and XDR Cloud Security provide comprehensive protection and can drastically reduce dwell time.
For further information: Barracuda Managed XDR and SOC.
This article was originally published at Barracuda Blog.
Photo: Halfpoint / Shutterstock




Barracuda Managed XDR effectively combines AI-driven detection, automation, and 24/7 SOC support to swiftly counter sophisticated threats, as shown by the quick mitigation in this case. However, enhancing proactive defenses across all layers, like servers and cloud, could further reduce early-stage vulnerabilities.
Great ‘playbook’ of response. But also, a stark reminder to 3x check our work to ensure ALL endpoints are protected!
XDR is a great feature and does a propper job when detecting intrusions.
Thanks for this incident description. These kinds of attacks usually happen when one least suspects it, and at the busiest times when people may be slightly off their guard.
It is very interesting and telling to see how long the malicious actors were able to operate undetected in the network (over 2 hours) and how quickly they were detected and thwarted once they tried to access an endpoint that was monitored and protected by XDR Endpoint Security! Definitely makes the case for the broadest deployment of XDR Endpoint Security possible!