
 Take a look at this edition of ‘The SOC case files’ to see how Barracuda’s Managed XDR team recently helped two companies mitigate incidents where attackers compromised computers and install rogue ScreenConnect remote management software. The incidents were neutralized before the attackers were able to move laterally through the network.
Take a look at this edition of ‘The SOC case files’ to see how Barracuda’s Managed XDR team recently helped two companies mitigate incidents where attackers compromised computers and install rogue ScreenConnect remote management software. The incidents were neutralized before the attackers were able to move laterally through the network.
Incident summary
- Two different organizations spotted odd behavior on computers. One company found open tax software, and the other spotted unusual mouse movements.
- In both cases, SOC analysts found rogue deployments of the ScreenConnect remote access and management software.
- In Company A, there were signs of possible data exfiltration attempts linked to a convoluted series of malicious downloads.
- Company B had evidence of malicious scripts and persistence techniques.
- In both cases, ScreenConnect was installed surreptitiously with the installer masquerading as files related to Social Security matters.
- SOC analysts were able to help both companies contain and neutralize the incidents.
How the attack unfolded
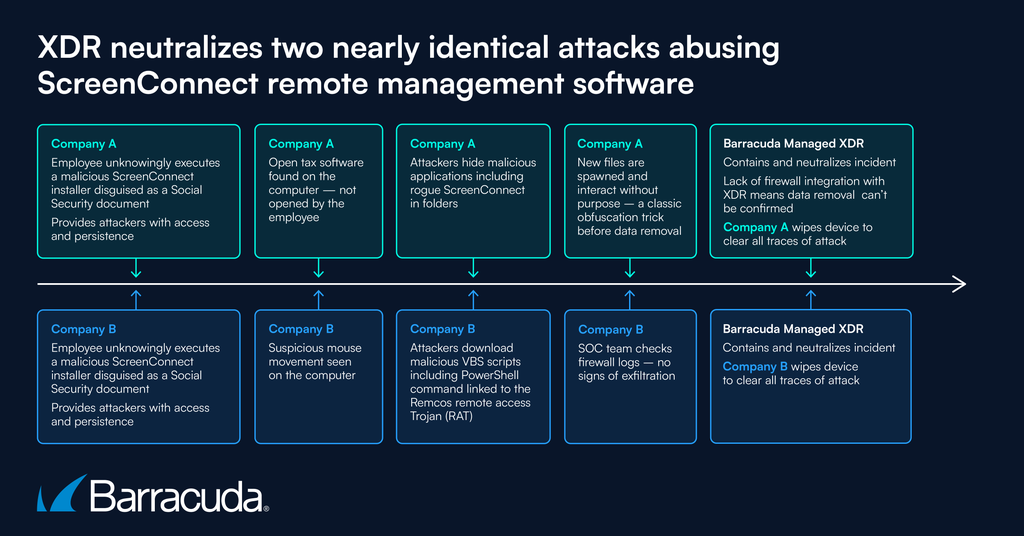
Company A
- Company A became suspicious when it noticed the tax software opened on a computer, which the user said they hadn’t opened.
- Barracuda Managed XDR’s SOC team checked the logs and identified the opened tax software linked to a ScreenConnect deployment.
- Working with Company A’s managed service provider (MSP), the SOC team confirmed the ScreenConnect deployment was unauthorized and is not part of the environment.
- The rogue application had been installed by the computer’s user. They had unknowingly executed a malicious ScreenConnect installer disguised as a Social Security document.
- The attackers were using ScreenConnect to establish and maintain access to the system.
- Additional executable files were found in the compromised user’s “downloads” folder, while the rogue ScreenConnect application was found hiding in two folders, the “Local\Apps\2.0\” folder and the “\Windows\SystemTemp\” folder.
- The SOC team spotted new files spawning and interacting with each other with no clear purpose. Such file creation loops and interactions between programs often represent an attempt at obfuscation to hide other activity, such as the unauthorized removal of data.
- As Company A’s XDR deployment lacked firewall integration, the investigation could not confirm whether there were any signs of data exfiltration.
- The SOC team advised Company A to completely wipe and rebuild the infected device to remove all traces of the attackers and their tools.
Company B
- Company B spotted random mouse movements on a computer, which led them to a rogue installation of ScreenConnect.
- The takeover was similar to Company A’s: An unwary end user had downloaded a supposed Social Security file that was actually a ScreenConnect installer.
- The attackers then created a new folder into which they downloaded further rogue software such as VBS scripts (a lightweight Microsoft programming language often used for web applications and automated tasks).
- One of these, “Child-Backup.vbs” executed a heavily obfuscated PowerShell command to establish persistence leveraging Remcos malware. Attackers use Remcos malware, an advanced remote access Trojan (or RAT), to control and monitor Windows computers.
- The SOC team checked all firewall logs and saw no signs of data exfiltration.
- The SOC team advised Company B to completely wipe and rebuild the infected device to remove all traces of the attackers and their tools.
Lessons learned
- Organizations need a robust, cyber-resilient security strategy to prevent malicious access and mitigate the impact of compromised accounts and endpoints.
- Endpoint monitoring and logging is imperative for security teams to spot rogue software installations and unauthorized remote access tools.
- In cases where attackers misuse a trusted application already deployed by an organization, the malicious intent of everyday IT actions such as file downloads may not always trigger a security alert. The security strategy should also include malware detection and prevention measures to uncover obfuscated scripts and persistence techniques.
- Equally important is employee cybersecurity awareness about the latest phishing techniques and safe browsing to mitigate social engineering attacks.
- Wiping compromised systems can be a controlled measure to eliminate threats if the attackers have managed to achieve persistence.
Barracuda Managed XDR helps to detect and mitigate such incidents. It continuously monitors endpoints and network activity to spot anomalous behaviors such as rogue software installations or unusual file interactions. It leverages threat intelligence to detect known malicious scripts and tools, such as Remcos malware or obfuscated PowerShell commands.
Managed XDR further provides rapid incident response capabilities, ensuring swift containment and remediation of identified threats. Detailed logs and forensic analysis help trace the origin and scope of the attack, enabling strategic future prevention measures.
By integrating with endpoint detection and response (EDR), Managed XDR enhances visibility into isolated systems and provides actionable insights for mitigation. Proactive threat hunting supported by Managed XDR helps identify persistence mechanisms and eliminate them before attackers gain sustained access.
Visit the website for more information on Barracuda Managed XDR and SOC. For the latest on new features, upgrades, and new detections for Barracuda Managed XDR, check out the most recent release notes.
This article was originally published at Barracuda Blog.
Photo: apops / Shutterstock

