
 The first few months of 2025 saw a massive spike in phishing-as-a-service (PhaaS) attacks targeting organizations around the world, with more than a million attacks detected by Barracuda systems in January and February.
The first few months of 2025 saw a massive spike in phishing-as-a-service (PhaaS) attacks targeting organizations around the world, with more than a million attacks detected by Barracuda systems in January and February.
The attacks were powered by several leading PhaaS platforms, including Tycoon 2FA, EvilProxy, and Sneaky 2FA. Between them, these three platforms show how PhaaS is evolving to become ever more complex and evasive.
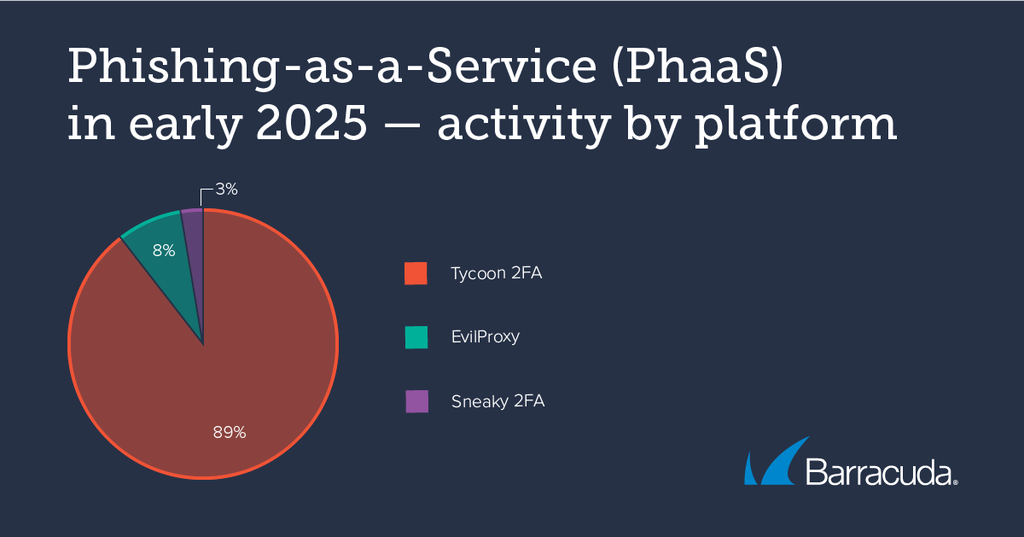
Tycoon 2FA was the most prominent and sophisticated PhaaS platform active in early 2025. It accounted for 89% of the PhaaS incidents seen in January 2025. Next came EvilProxy, with a share of 8%, followed by a new contender, Sneaky 2FA with a 3% share of attacks.
The further evolution of Tycoon 2FA
In the middle of February 2025, Barracuda threat analysts noticed an outbreak of attacks using Tycoon 2FA. The investigation revealed that the platform has continued to develop and enhance its evasive mechanisms, becoming even harder to detect.
Technical details
In a previous blog post about Tycoon 2FA, analysts discussed the malicious scripts used to obstruct analysis of the phishing pages by defenders, for example by blocking shortcut keys.
The developers have now abandoned that approach and replaced it with something even more evasive.
- The upgraded script is encrypted with a Caesar cypher — a shifting substitution cypher — instead of being in plain text. This script is responsible for several processes, such as stealing user credentials and exfiltrating them to an attacker-controlled server.
- Several examples of the script include Hangul Filler (or Unicode 3164), which is an invisible character (but not a space) from the Hangul script. These characters are often used to fill space without displaying any content and are commonly employed in phishing obfuscation techniques.
- The upgraded script identifies a victim’s browser type, likely for evasion or attack customization. It also includes Telegram links. These are often used to secretly send stolen data to attackers. This script also contains intercommunication links such as Ajax requests, which enable parts of a web page to be updated independently of the rest of the page, and the script features AES encryption to disguise credentials before exfiltrating them to a remote server, making detection more difficult.
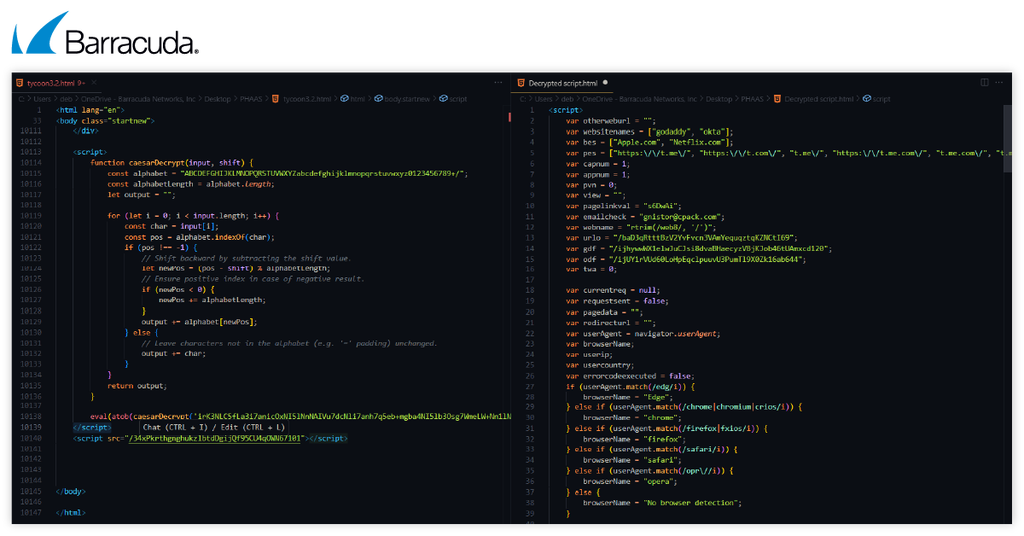
Left: Cesar encrypted script – Right: After decryption
EvilProxy — a dangerously accessible tool
EvilProxy is a particularly dangerous PhaaS because it requires minimal technical expertise, making sophisticated phishing attacks accessible to a wider range of cybercriminals.
EvilProxy enables attackers to target widely used services such as Microsoft 365, Google, and other cloud-based platforms. Through phishing emails and malicious links, EvilProxy tricks victims into entering their credentials on seemingly legitimate login pages.
Technical details
- EvilProxy phishing attacks employ a reverse proxy configuration. A reverse proxy is a server that sits in front of web servers and forwards client (e.g., web browser) requests to those web servers. This reverse proxy serves as a bridge between the attacker, the victim, and the target service.
- When victims enter their credentials into the fake login page, their credentials are passed to the legitimate website. This provides the attacker with live access to the user’s account without arousing suspicion.
- The source code used by EvilProxy for its phishing webpage closely matches the source code of the original, legitimate login page. This makes it difficult to distinguish from the original, legitimate website.
In the visual below, the source code of the legitimate Microsoft login webpage is on the left, while that of the EvilProxy phishing webpage is on the right.
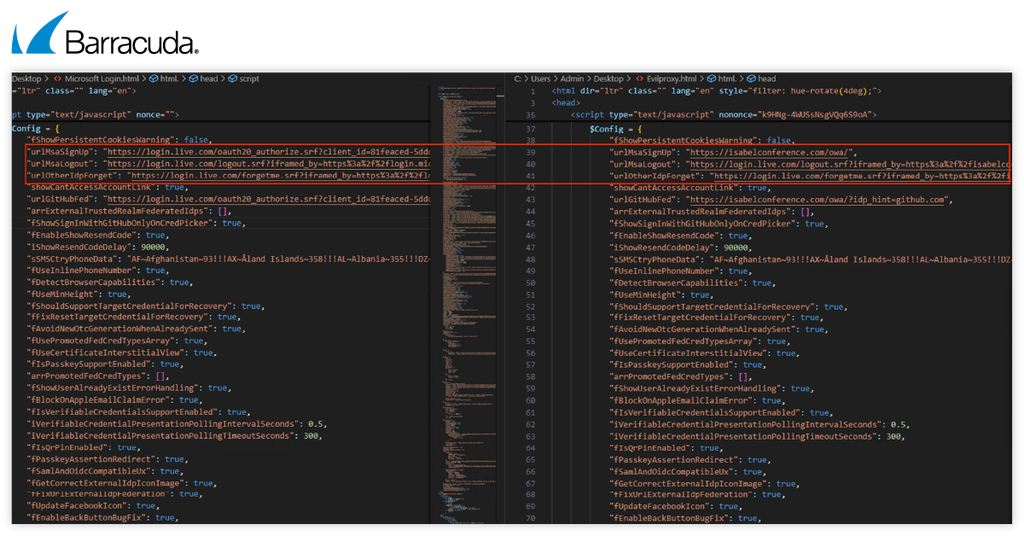
Left: Legitimate Microsoft login source code – Right: EvilProxy source code
Sneaky 2FA helpfully fills in phishing form for victims
The third most prominent PhaaS in early 2025 was Sneaky 2FA, the platform for adversary-in-the-the-middle (AiTM) attacks targeting Microsoft 365 accounts in search of credentials and access.
Targets receive an email that contains a link. If they click on the link, it redirects them to a spoofed, malicious Microsoft login page. The attackers check to make sure the user is a legitimate target and not a security tool before pre-filling the fake phishing page with the victim’s email address by abusing Microsoft 365’s ‘autograb’ functionality.
The attack toolkit is sold as-a-service by the cybercrime outfit, Sneaky Log. It is known as Sneaky 2FA because it can bypass two factor authentication. Sneaky 2FA leverages the messaging service Telegram and operates as a bot.
Technical details
- The attackers’ phishing URL includes the target’s email address as a parameter, either in plain text or encoded in Base64 (which enables binary data such as images or files to be turned into a text format and transmitted over media that only support text, such as email or URLs.) For example: hxxps://phishing_url/00/#email_id
- The Sneaky 2FA phishing URLs usually comprise 150 alphanumeric characters, followed by the path /index, /verify and /validate.
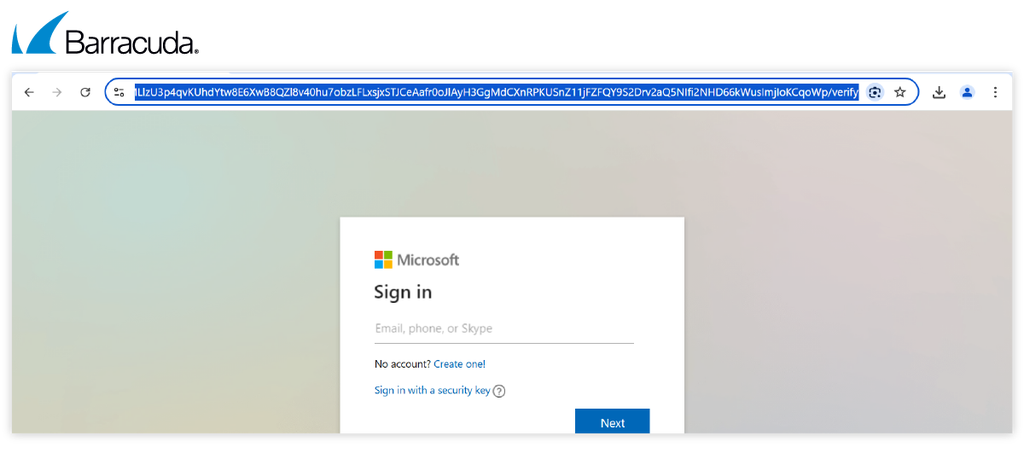
This pattern allows the attackers to track visitors to its fake Microsoft login pages and to filter out the targets it doesn’t want because they are unlikely to be legitimate users and potential victims.
- Sneaky 2FA attackers try to determine whether a visitor’s IP address originated from a data center, cloud provider, bot, proxy, or VPN or is associated with known abuse. If the server considers that the visitor’s traffic does not match that generated by targeted victims, the phishing kit redirects the visitor to a Microsoft or Windows-related Wikipedia page using the href[.]li redirection service. We can see this redirection script within the <noscript> element of the source code.
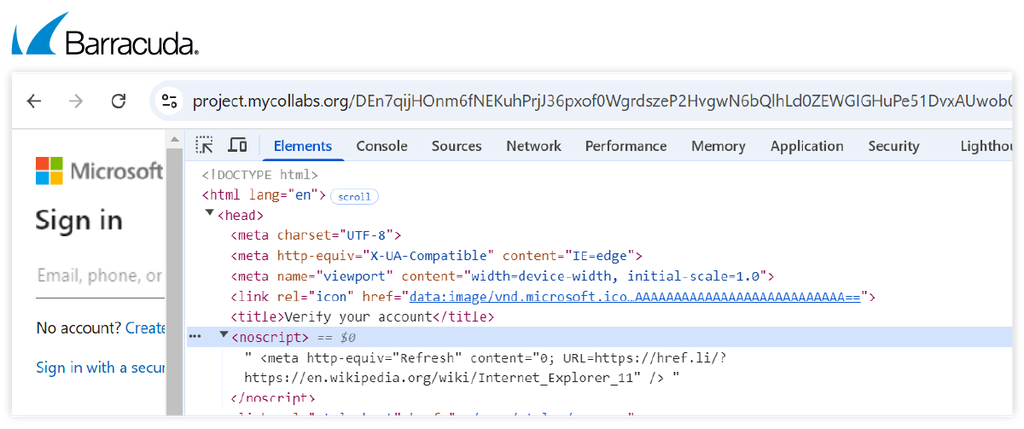
Wikipedia redirection
How to spot a PhaaS attack
Avoid entering your credentials if:
- A login page includes a “.ru” top-level domain (the last part of a URL), and the victim’s email ID is embedded in the phishing URL either in the form of plain text or Base64-encoded. These clues could indicate a Tycoon 2FA attack.
- EvilProxy attacks are harder to detect because they use a random URL. However, if you think the Microsoft/Google login page URL is different from the usual login page, avoid entering your credentials. Another giveaway is unusual MFA prompts, such as receiving MFA prompts when you are not actually logging in.
- To detect Sneaky 2FA, check if the webpage URL contains a 150 alphanumeric string followed by either /verify, /index, or /validate at the end of the URL.
Strengthening email security
Phishing emails are the gateway for many attacks, from credential theft to financial fraud, ransomware, and more. The platforms that power phishing-as-a-service are increasingly complex and evasive, making phishing attacks both harder for traditional security tools to detect and more powerful in terms of the damage they can do.
An advanced, defense-in-depth email security solution, such as Barracuda Email Protection is vital, and it should be equipped with multilayered, AI/ML-enabled detection to protect organizations and employees against PhaaS-based attacks.
Security awareness training for employees that helps them to understand the signs and behaviours of the latest threats is also important. Encourage employees to report suspicious-looking Microsoft/Google login pages. If you find them, undertake an in-depth log analysis and check for MFA anomalies.
These elements should be complemented by robust and consistent security access and authentication policies and a phishing-resistant MFA solution such as FIDO2 security keys.
Ashitosh Deshnur, Associate Threat Analyst at Barracuda contributed to the research for this blog post.
This article was originally published at Barracuda Blog.
Photo: instaphotos / Shutterstock


Implementing additional email security controls and providing user training can reduce the risk of falling victim to phishing attacks.
Thanks for this most informative post.
I remember years ago doing Vishing training campaigns for my users. I hope that it helped them deal with attacks like these.
Nice, thorough article
This article really highlights just how serious the phishing-as-a-service (PhaaS) threat has become. The fact that over a million attacks were recorded in just two months is pretty alarming. It’s especially concerning to see how these platforms, like Tycoon 2FA and EvilProxy, are getting more advanced and harder to detect. It just goes to show how important it is for businesses and individuals to stay ahead with strong security measures, better awareness, and smarter tools to fight back against these evolving threats. Cybercriminals aren’t slowing down, so we can’t afford to either.
Great insights on how to discern an attack. Stunning how crafty these methods have become!
Barracuda and other email monitoring programs have to ramp it up during certain times as well to keep up with the hackers. Dial it up to 11 towards the end of the day for users to not be paying attention and will click on anything.
Thank you so much for this great information!
thanks for bringing this to the forefront, as this is becoming a prevalent vector to be aware of.