 As defenders tighten their grip on the tools and techniques used in phishing attacks, adversaries are finding new ways to bypass detection and target potential victims. For example, many phishing attacks rely on convincing users to click on a compromised link that leads them to a webpage where attackers try to harvest their credentials.
As defenders tighten their grip on the tools and techniques used in phishing attacks, adversaries are finding new ways to bypass detection and target potential victims. For example, many phishing attacks rely on convincing users to click on a compromised link that leads them to a webpage where attackers try to harvest their credentials.
Security tools have become more effective at spotting such links, so attackers started deploying techniques such as URL obfuscation using legitimate shortlink services to conceal malicious links. These techniques are now evolving into highly crafted technical approaches that leverage brand and domain reputation.
Barracuda researchers recently uncovered a range of phishing attacks that abuse legitimate URL protection services to conceal the malicious URL and trick unwary users into clicking on the link.
Turning URL protection on itself
From mid-May 2024 onwards, Barracuda researchers observed phishing attacks taking advantage of three different URL protection services to mask their phishing URLs. The services are provided by trusted, legitimate brands. To date, these attacks have targeted hundreds of companies, if not more.
URL protection services work as follows: If a URL is included in an email, the service copies it, rewrites it, and then embeds the original URL within the rewritten one.
When the email recipient clicks on the “wrapped” link, it triggers an email security scan of the original URL. If the scan is clear, the user is redirected to the URL. In the attacks seen, the users were redirected to phishing pages designed to steal sensitive information.
How attackers may gain access to service
It is probable that the attackers gained entry to the URL protection services — either intentionally or opportunistically — after compromising the accounts of legitimate users.
Once the attacker has taken over an email account, they can impersonate the owner, and infiltrate and examine their email communications, also known as business email compromise (BEC) or conversation hijacking.
Links in emails connected to the account, or in the user’s email signature, will reveal whether a URL protection service is being used, and which one.
To leverage the URL protection to rewrite their own phishing URLs, the attackers would need to either have access to internal systems to get the phishing URL rewritten, which is exceedingly rare, or more likely send an outbound email to themselves using the compromised accounts, with the phishing link in the mail.
While delivering that message the relevant email security solution installed by the user will rewrite the phishing URL using their own URL protection link. The attacker can then use that link to conceal malicious URLs in their phishing campaigns.
The URL protection providers may not be able to validate whether the redirect URL being used by a specific customer is really being used by that customer or by an intruder who has taken over the account.
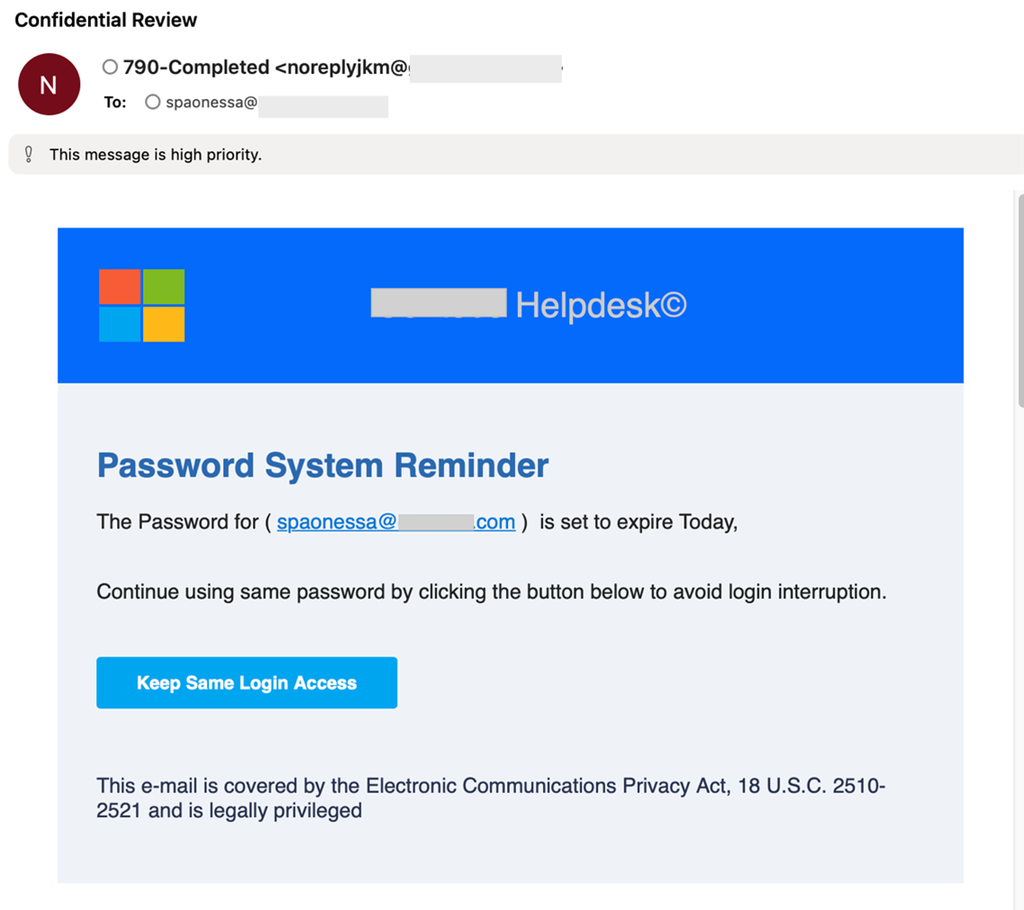
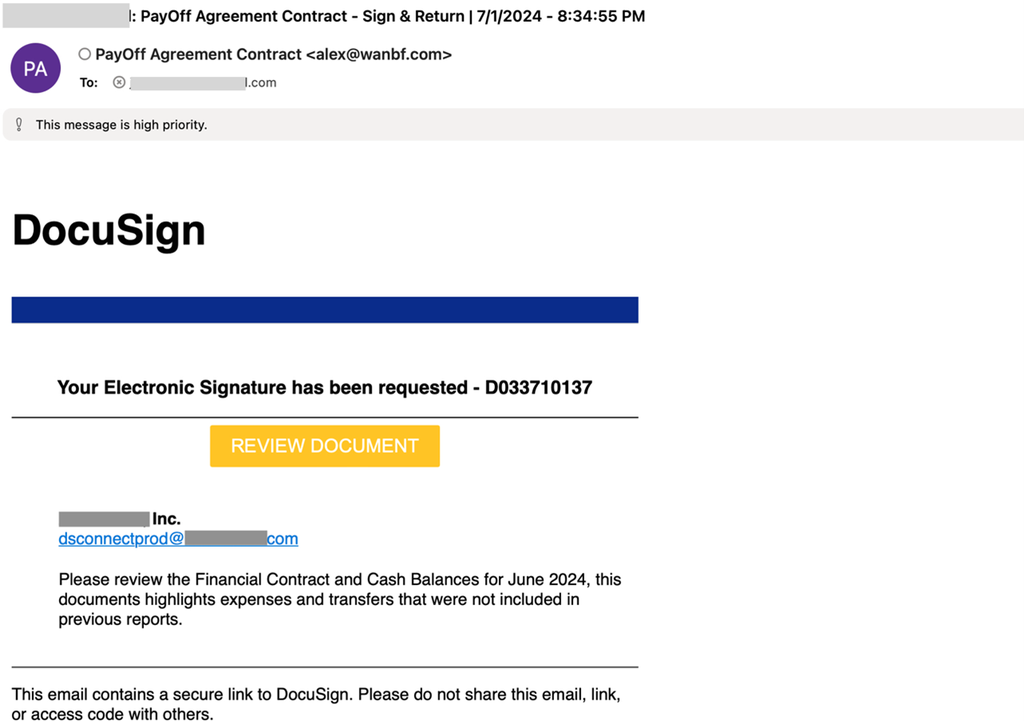
The malicious URL links were included in emails from domains such as wanbf[.]com and clarelocke[.]com, designed to look like DocuSign and password reset reminders.
Conclusion
Traditional email security tools may find it difficult to detect these attacks. The most effective defense is a multilayered approach, with various levels of security that can detect and block unusual or unexpected activity, however complex. Solutions that include machine-learning capabilities, both at the gateway level and post-delivery, will ensure companies are well protected.
As with all email-borne threats, security measures should be complemented by active and regular security awareness training for employees on the latest threats and how to spot and report them.
This article was originally published at Barracuda Blog.
Photo: chainarong06 / Shutterstock

