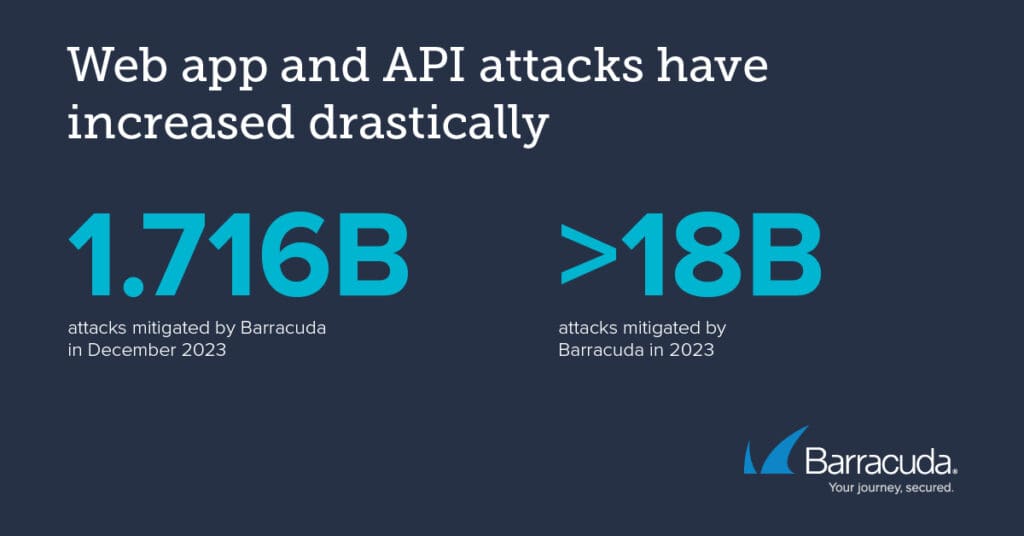
 The number of attacks targeting web applications and application programming interfaces (APIs) has increased significantly. Barracuda mitigated more than 18 billion attacks against applications during 2023, including 1.716 billion in December alone.
The number of attacks targeting web applications and application programming interfaces (APIs) has increased significantly. Barracuda mitigated more than 18 billion attacks against applications during 2023, including 1.716 billion in December alone.
Web applications are computer programs that are accessed through a web browser. Good examples are Microsoft 365 and Google Docs/Gmail. Web applications offer many business benefits, such as speed, compatibility, and scalability.
They are also a prime target for cyberattack. According to the latest DBIR, web applications were the top action vector in 2023, used in 80 percent of incidents and 60 percent breaches.
Why web applications are a top target for attack
There are two main reasons. First, many web applications carry vulnerabilities or configuration errors. Second, many contain extremely valuable information, such as personal and financial data – and a successful breach will give attackers direct access to that data. Barracuda research shows that 40 percent of IT professionals who’ve been involved in ethical hacking believe web application attacks are among the most lucrative for cyber-attackers, and 55% say the same for APIs.
The top OWASP attacks targeting web applications
To understand where attackers are focusing their time and resources, we took a deep dive into the web application incidents detected and mitigated by Barracuda Application Security during December 2023.
We focused on attacks identified by the Open Worldwide Application Security Project (OWASP).
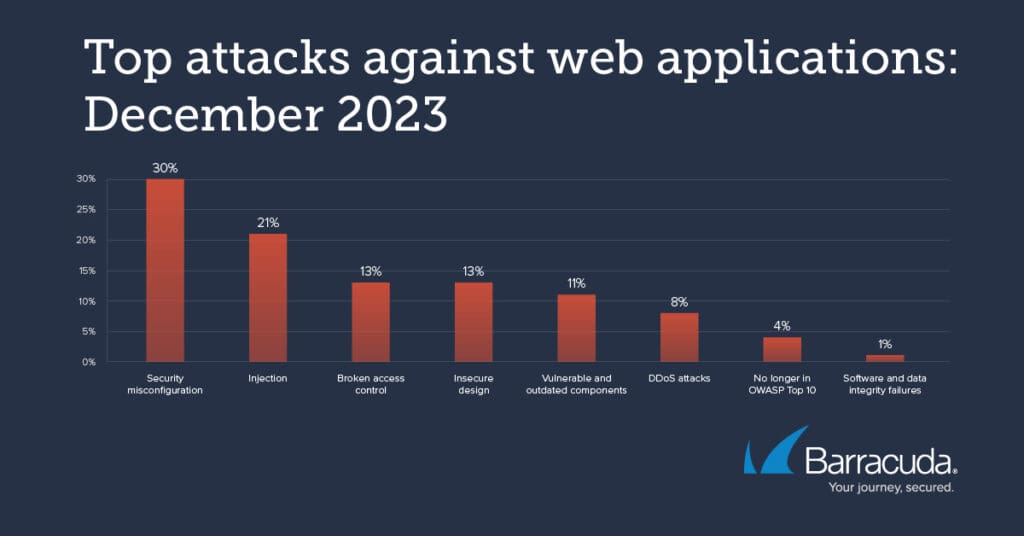
This is what we found:
- 30 percent of all attacks against web applications targeted security misconfigurations – such as coding and implementation errors.
- 21 percent involved code injection. These were more than just SQL injections (generally designed to steal, destroy, or manipulate data.) Log4Shell and LDAP injection attacks were also popular. LDAP is used by organizations for privilege management, resource management, and access control, for example to support single sign on (SSO) for applications.
The OWASP Top 10 list is updated annually. It is worth noting that there have recently been a few changes to the OWASP Top 10 list. These mainly involve the integration of ‘top level’ attack tactics into other categories. Examples include cross-site scripting (XSS) and cross-site request forgery (CSRF) which enable attackers to steal data or trick the victim into performing an action that they do not intend to. Both tactics are still being used in significant numbers. XSS, in particular, is being widely used by entry level bug bounty hunters or hackers trying to break into networks.
Beware the bots
Barracuda’s anti-botnet detection data shows that the majority (53 percent) of bot attacks targeting web applications in December 2023 were volumetric distributed denial of service (DDoS) attacks.
Volumetric DDoS attacks are generally launched by vast botnets of connected devices (IoT). The attacks are based on brute force techniques that flood the target with data packets to use up bandwidth and resources. It’s worth noting that such attacks can be used as a cover for a more serious and targeted attack against the network.
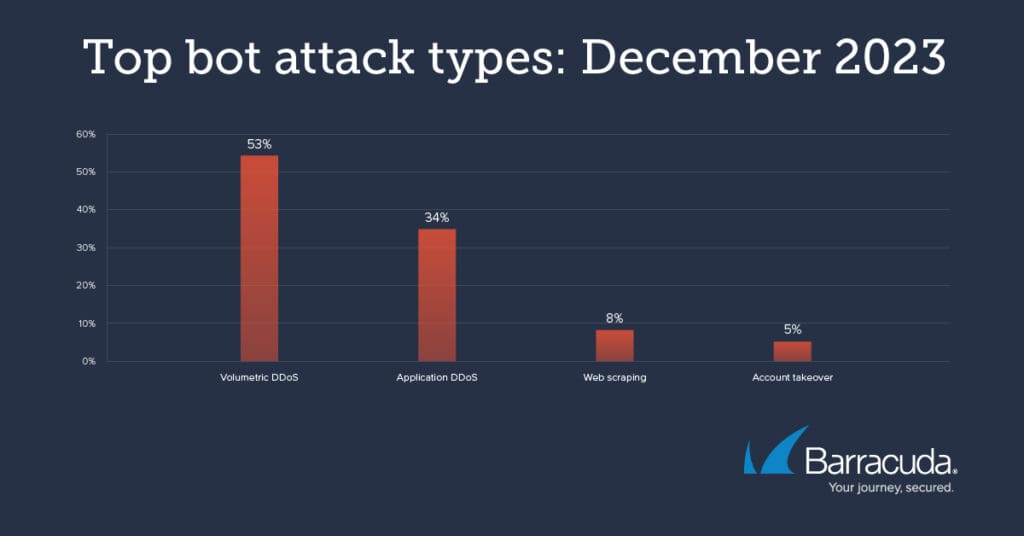
The data also shows that around a third (34 percent) of bot attacks were application DDoS attacks, targeting a specific application, and 5 percent were bot-driven account takeover attempts.
The account takeover attacks are detected with Machine Learning and Barracuda’s Privileged Account Protection capability. The Privileged Account Protection examines login patterns to detect anomalies and warn security administrators about any unusual activity that could be an attack. This means that incidents are blocked at an early stage.
Vulnerable and outdated app components
Vulnerable and outdated components in applications are the gifts that keep giving for attackers. The ProxyShell vulnerabilities complex from 2021 has been continuously exploited, leading to a number of high-profile breaches, including ransomware.
There are some older, less prominent vulnerabilities that are targeted from time to time by threat actors – like the current Androxgh0st Malware, for which the U.S. Cybersecurity and Infrastructure Agency (CISA) issued a warning on 16 January 2024.
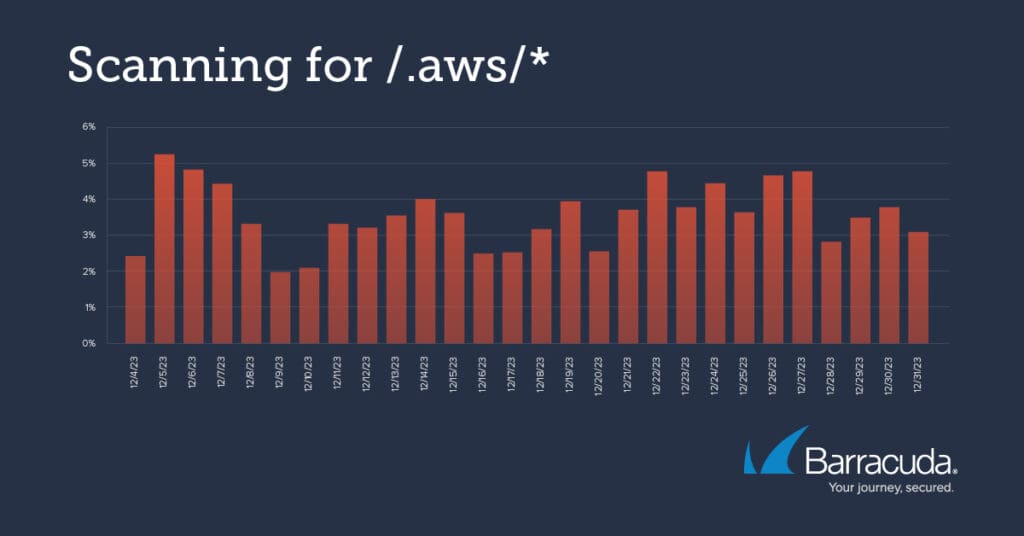
The following common vulnerabilities and exposures (CVEs) have been detected in significant numbers probing Barracuda installations over the last few months. The graphs show that the scan attempts started at roughly the same time for all these vulnerabilities, with similar peaks – suggesting there is a single or coordinated attack campaign underway.
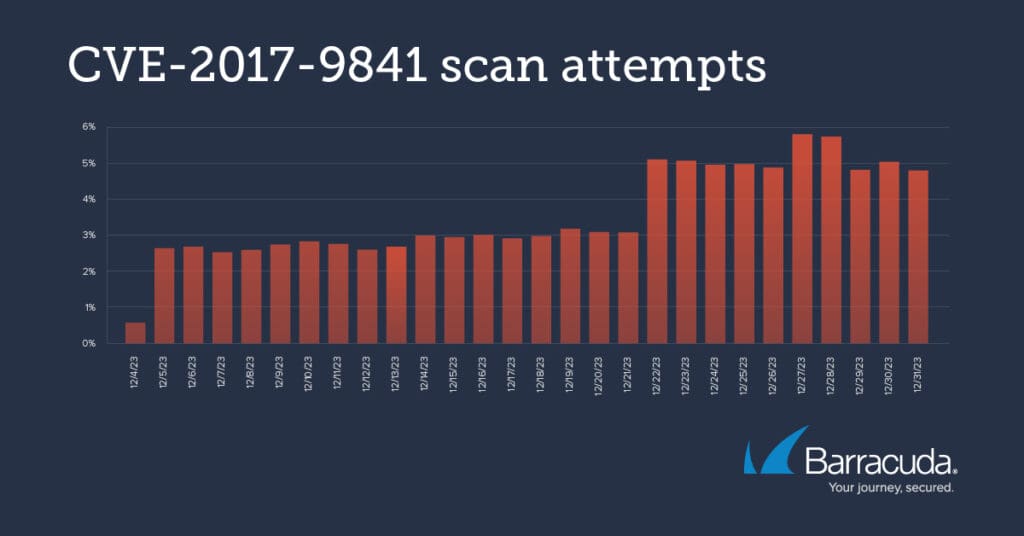
CVE-2017-9814 is a high severity (7.5) vulnerability that enables attackers to implement a denial-of-service attack. The vulnerability was modified in 2023.
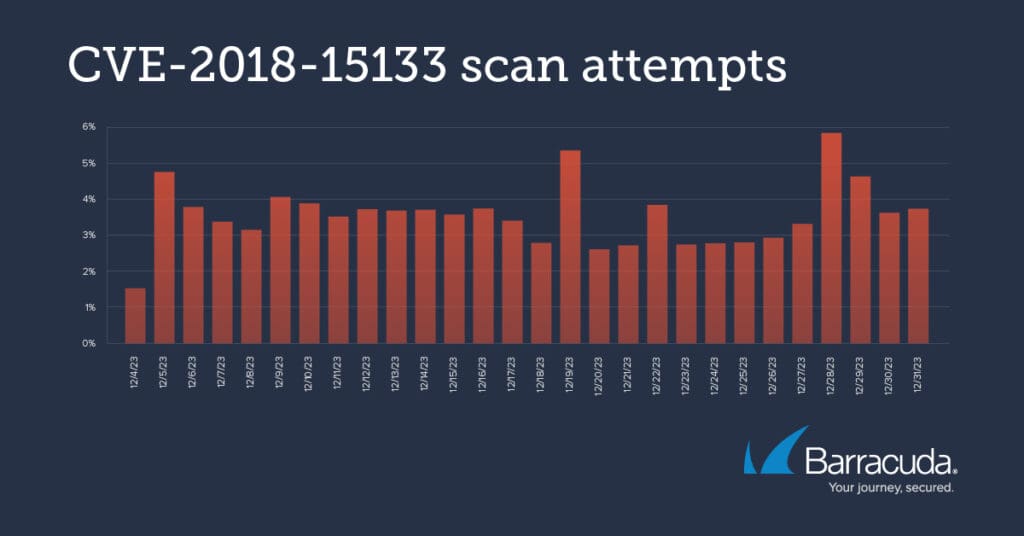
CVE-2018-151333 is a high-severity (8.1) remote code execution vulnerability in the Laravel framework, which has also been recently modified.
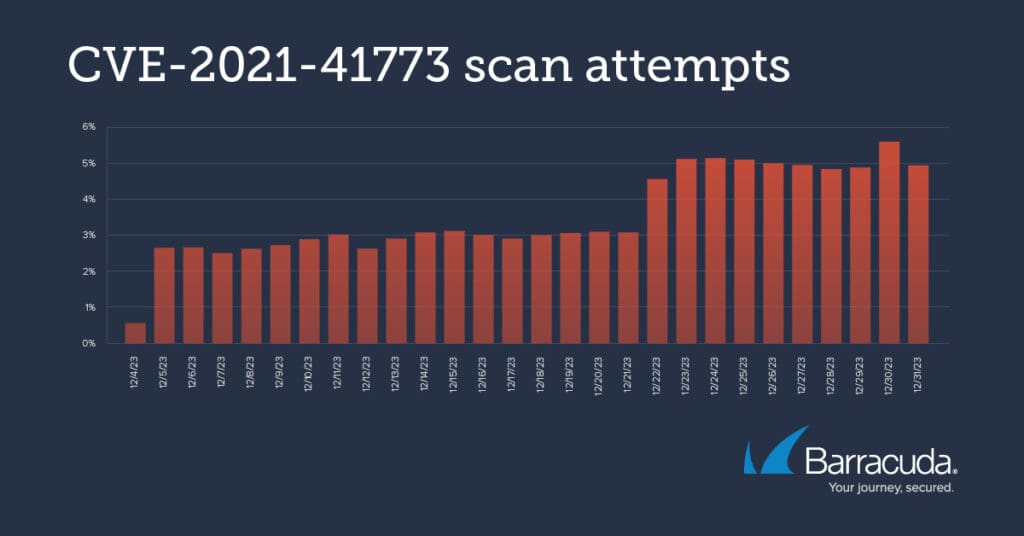
CVE-2021-41773 is a high severity (7.5) Apache HTTP server vulnerability that was also modified in 2023.
The source of scans
These are the countries that scans from these vulnerabilities are coming from.
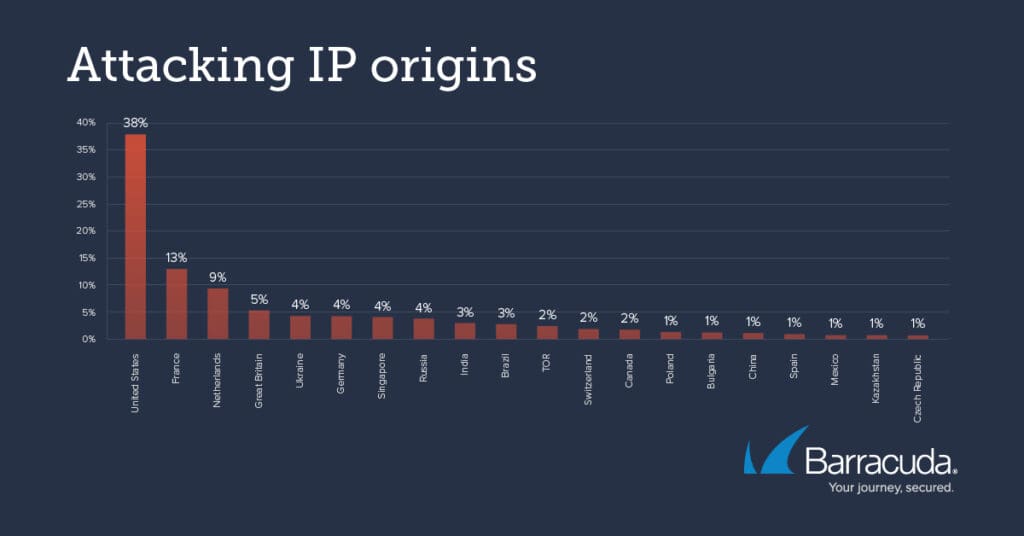
It is interesting to see the slightly higher number of Tor IP’s being blocked, as well as the U.S. numbers. The high proportion of scans emanating from the U.S. is likely to reflect the fact that many of the attacks come from public servers that are U.S.-based.
It is also interesting to see the regional changes over time. In early December, Tor was among the top 5 ‘regions’, but it dropped off the list as the month progressed – likely because of how often there is complete block for Tor.
Filtering out the noise
Our log analysis revealed the proportion of probes or scans were perpetrated by attackers versus background noise.
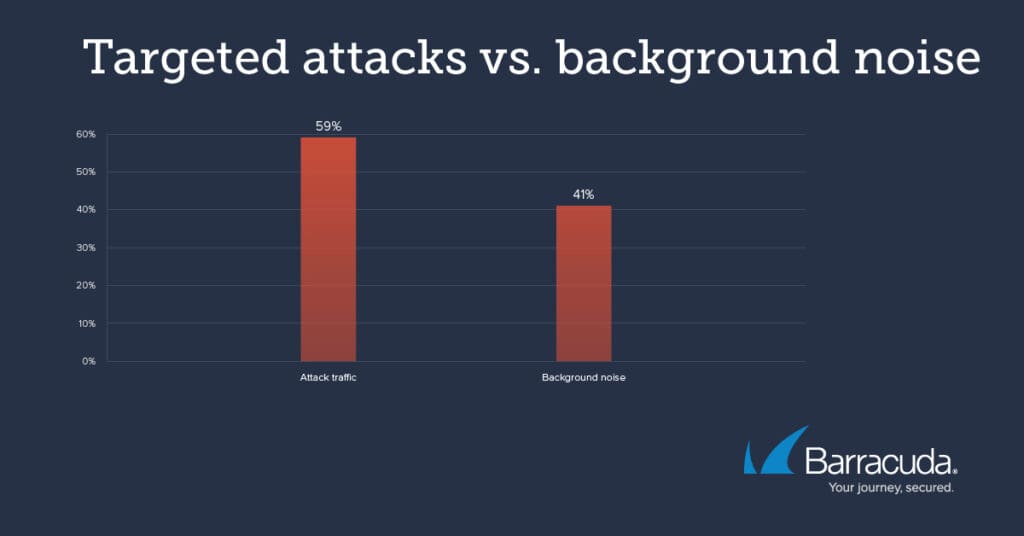
Background noise in this case is relatively benign scanning by various CERTs, Shodan etc., while attack traffic represents attackers – automated and otherwise – attempting to perform actual attacks. In the case of these three vulnerabilities, the ratio is much more towards valid attack traffic versus scanning.
Securing your applications
As mentioned above, web applications and APIs are lucrative attack vectors for cybercriminals – and they are coming under increasing attack.
Defenders are hard pressed to keep up with the growing number of vulnerabilities. They have to contend with both zero-days and older vulnerabilities. The software supply chain for critical apps may also have vulnerabilities – as demonstrated by the Log4Shell vulnerability.
Attackers will often target old vulnerabilities that security teams have forgotten about to try and breach an overlooked, unpatched application and then spread into the network.
How Barracuda can help
Think of application protection as a defensive “onion” – with multiple layers to detect and prevent an incident from escalating. Barracuda Application Protection covers multiple parts of that defensive strategy, offering web application & API protection, DDoS protection, bot protection including account takeover protection, and much more. You can also schedule a demo here.
Photo: antoniodiaz / Shutterstock

