 The year 2021 continues to see a surge in ransomware as the world’s cyber ecosystem begins to ease into a post-pandemic phase. The education and healthcare sectors remain particularly vulnerable to ransomware as hackers attempt to squeeze more out of their victims.
The year 2021 continues to see a surge in ransomware as the world’s cyber ecosystem begins to ease into a post-pandemic phase. The education and healthcare sectors remain particularly vulnerable to ransomware as hackers attempt to squeeze more out of their victims.
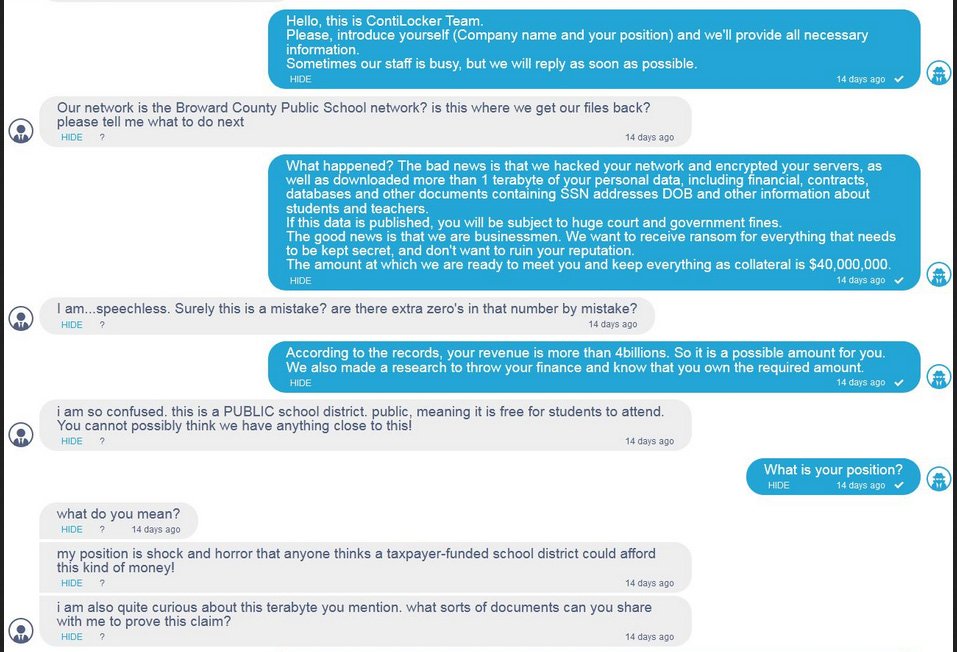
Last month, Broward County Public Schools in Florida, one of the nation’s largest school systems, was the target of a ransomware attack. The Conti gang demanded $40,000,000.00, the second-highest ransom ever requested in a ransomware attack. The one “silver lining” of the increase in ransom demands is that hackers are raising the ransoms to give themselves as much “cushion” as possible, knowing full well that negotiations downward will trend downward.
Broward County Public Schools balked at paying such a sum and negotiated with the hackers. Eventually, the negotiations broke down, which is when Conti released screenshots of the back and forth. The exchange is startling in its frankness and captures the helplessness of the school district in a way rarely seen, since most negotiations happen behind closed doors.
Ransomware is not going away
Alan Perez, the founder of Genesis CyberSolutions in Key West, calls ransomware the most significant threat of 2021, especially to public institutions like school systems. Smarter MSP caught up with him to ask why he views it as such a threat and to get his thoughts on best practices for mitigation.
Perez believes the government and other public facilities are particularly vulnerable to a ransomware attack right now. “There needs to be more awareness among employees on how the attack is delivered and executed, as well as how to respond appropriately and timely,” Perez advises. In the case of the Broward County attack, it has not been determined or announced how the hackers got in, but phishing continues to be the most common method.
One of the reasons driving the increased attacks in 2021 despite companies becoming more resistant to paying is that the attacks are getting easier and cheaper for hackers to deliver. Perez says that digital currency has made ransomware seamless and more effortless for hackers to cover their tracks. And now, AI is going to increasingly aid them.
“Hackers are developing AI that can do the work for them and take advantage of the new age of currency and Blockchain,” he adds.
All of this will force CISOs, MSPs, and other security stakeholders to up their game in the ever-evolving ransomware threat protection methods. Perez notes that awareness needs to be expanded on how ransomware attacks are being delivered and how they behave.
“Employees need to be trained that ransomware can be delivered through many forms such as an attachment, USB infection, and social engineering utilizing forms in authority or intimidation as an employee or officer of the company,” Perez says.
Employees can plug in devices without realizing they are infected, and inside actors can inflict damage. Recognizing social engineering tactics and confirming the individual is who they say they are, using something like an employee I.D. in email encryptions and verbal password of the day, would be a very safe package of mitigation measures, Perez advises.
More robust software solutions that recognize ransomware’s digital signatures are also part of the ever-expanding battle against ransomware. But simply intercepting the ransomware is only part of the solution.
Two steps to mitigate attacks in 2021
“If a file is suspected of being malicious, it should be sent to a team for reverse engineering of the ransomware or suspected software or file,” Perez suggests. Such action can, he estimates, possibly cut down 60 percent of ransomware attacks. Perez adds, “Because unfortunately the number one security weakness in the I.T. industry is the human element and always exposed to possibly being manipulated and hacked.”
The second step to staying ahead of ransomware is to report suspicious programs or system behavior as soon as possible (the team could be a red or blue internal team, an MSP, or CISO).
“The team from there should successfully disarm the ransomware by means of finding the program in the system and cutting off communication to that server or exposed tech,” Perez says.
If that is not an option, then, he advises, better technology should be implemented, such as AI to assist in removing such complex ransomware. “Doing this would save the industry millions of dollars and secrets that can damage the company’s image and it’s employees and investors,” Perez continues.
Perez says the best practice is to keep updated on new code and technologies because it seems bad actors are always hungry for success and the thrill of tackling a system and reaping the rewards. “They will do what it takes to learn and wreak havoc. That’s the psychology behind it. Do it for the high or monetary gain,” he concludes.
But for innocent enterprises on the receiving end, it is no laughing matter and 2021 appears to be another bad year for ransomware attacks. MSPs need to be on guard, especially for ones with clients in the healthcare and education verticals.
Photo: wk1003mike / Shutterstock

Great article Kevin. For healthcare providers, I would also suggest comprehensive HIPAA compliance and training programs, along with cyber insurance. Unfortunately, in today’s environment, it’s not a matter of if; it’s a matter of when an incident will occur.