

Greek mythology says the Medusa was once a beautiful woman until Athena’s curse transformed her into a winged creature with a head full of snakes. Because of her power to petrify anyone who looked directly upon her face, she is considered both a ‘monster’ and a protector. She’s a compelling character in a giant story that’s often told in bits and pieces.
Ransomware groups like to adopt identities that make them appear strong and powerful, and perhaps this was the group’s intent when it emerged as Medusa ransomware in late 2022. The group has been a top ten ransomware actor since 2023, claiming high-profile victims like Toyota Financial Services and the Minneapolis Public School District. I doubt anyone credits the Medusa-themed brand for that rise to the top of the ransomware underworld, but there’s no denying that cybercriminals like to use that name.
Medusa confusion
There are three other active and unrelated threats that use the name Medusa somewhere in their brands. These threats may show up in your results if you’re researching Medusa ransomware.
- Medusa Android Banking Trojan: This malware was first observed in 2020. The current version operates through a malware-as-a-service (MaaS) model and targets newer model phones. It can steal data, take screenshots, and drop additional malware on the victim’s device.
- Medusa Botnet: This is an old strain of malware, popping up on the darknet way back in 2015. It’s changed since then, and is now a distributed denial of service (DDoS) botnet that is based on the leaked Mirai code. This malware also has a ransomware function called ‘Medusa Stealer,’ which seems to have a bug in the code that makes this a wiper rather than ransomware.
- MedusaLocker ransomware: This was first observed in 2019 but remains a lesser-known threat than Medusa. The two ransomware threats are sometimes conflated in media coverage, which can lead to confusion around tactics, techniques, and procedures (TTP), indicators of compromise (IoC), and other information.
There is also Operation Medusa, which is not a threat actor. Medusa was the code-name for the 2023 international law enforcement disruption of the global Snake malware network. This law enforcement operation was not targeting any variant of Medusa ransomware.
Who is Medusa ransomware?
The exact location and individual operators of Medusa are unknown, but analysts suspect the group is operating out of Russia or an allied state. The group is active on Russian-language cybercrime forums and uses slang unique to Russian criminal subcultures. It also avoids targeting companies in Russia and Commonwealth of Independent States (CIS) countries. Most Medusa ransomware victims are in the United States, United Kingdom, Canada, Australia, France, and Italy. Researchers believe the Medusa ransomware group is supportive of Russian interests, even if it is not a state-sponsored group.
The primary motivation of the Medusa ransomware group appears to be financial gain. Like many groups, Medusa uses a double extortion strategy and begins negotiations with large demands. The group’s data leak site, TOR links, forums, and other key extortion resources reside on the dark web. This type of setup is common among threat actors.
What makes Medusa unique here is its use of the public internet, also referred to as the ‘clearnet’ or ‘clear web.’ Medusa is linked to a public Telegram channel, a Facebook profile, and an X account under the brand ‘OSINT Without Borders.’ These properties are run by operators using the pseudonyms ‘Robert Vroofdown’ and ‘Robert Enaber.’ There is also an OSINT Without Borders website.
OSINT Without Borders Telegram account banner
OSINT Without Borders X (formerly Twitter) profile run by Robert Vroofdown
These public-facing properties likely aim to exert more pressure on victims and spread awareness of the Medusa ransomware threat.
The Medusa ransomware group appears to operate independently with its own infrastructure. There’s no evidence that Medusa is a rebrand or offshoot of another group, and there are no reports of code similarities with other threats. However, experts have determined that the organized cybercrime group ‘Frozen Spider’ is a key player in the Medusa ransomware operation. Frozen Spider collaborates with other threat actors and is part of the larger cybercrime-as-a-service (CCaaS) ecosystem.
Medusa attack chain
Medusa relies heavily on initial access brokers (IAB) to accelerate their attacks. An IAB specializes in credential stuffing, brute force attacks, phishing, and any other attack that will get them into a company’s network. The initial access is all they want, because IABs make their money by selling this information to other threat actors.

IAB threat actor ‘DNI’ offers initial access to US companies, via Dark Web Informer
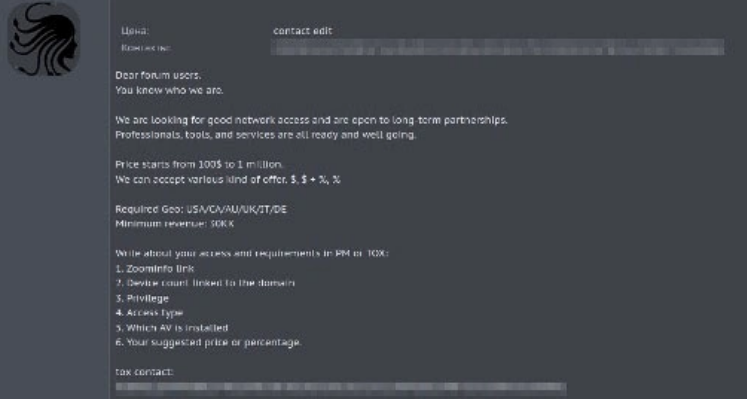
Medusa post on cybercrime forum requesting “good network access” for targets in “USA/CA/AU/UK/IT/DE”
You can think of the IAB as part of the supply chain for other cybercriminals. Ransomware groups like Medusa make their money by stealing and encrypting data, so they’d rather buy access to a network than spend time trying to break in. The IAB and ransomware operator collaboration is one of the most effective cybercrime accelerators in the modern threat landscape.
Medusa operators will also conduct phishing campaigns and exploit public-facing vulnerabilities. IABs make ransomware operations more efficient, but Medusa and other threat operators will conduct their own intrusion attacks when necessary.
Once inside the system, Medusa will try to expand its footprint by moving laterally and escalating privileges. It will also initiate OS credential dumping techniques to harvest more credentials from within the network. These techniques are just different methods designed to steal credential information from legitimate operating system (OS) functions. We’ll dig into them in a future post.
Medusa scans the network, looking for exploitable systems and other resources that it can access with the stolen credentials. This is a good example why you should apply the principle of least privilege (PoLP), and keep your internal systems patched and secured even if they’re not exposed to the public internet. And don’t forget that support for Windows 10 ends in October 2025, so you’ll want to upgrade, replace, or purchase extended support for those machines.
Medusa uses PowerShell and other tools to disable defenses, explore the network, and escalate its privileges. It prepares for data exfiltration by launching its ransomware binary, gaze.exe. This loads the processes that create the environment for exfiltration, while PowerShell scripts and supporting tools handle the actual data transfer. Medusa uses TOR secure channels to copy the victim’s data and announce the attack on its dark web leak site, Medusa Blog.
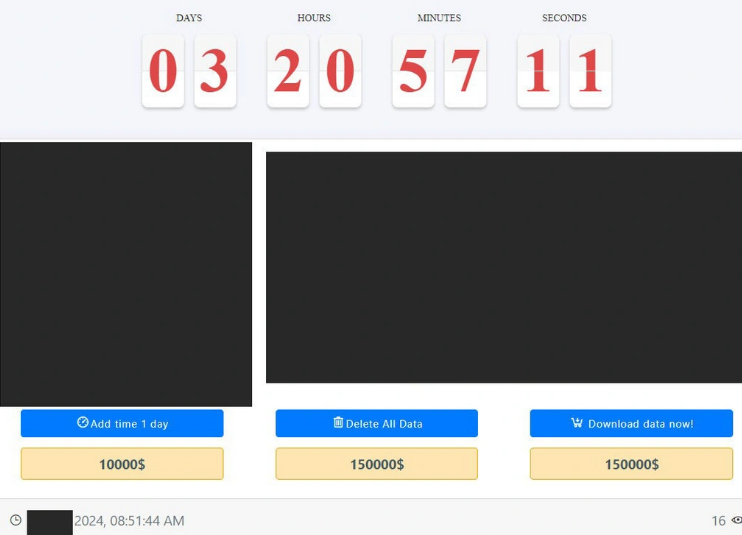
Medusa blog post showing victim information (redacted), countdown timer, and menu of options
The Medusa encryption process adds the .MEDUSA extension to each of the affected files, and creates a ransom note in each folder that holds encrypted files. The ransom note, named !!!READ_ME_MEDUSA!!!.txt, contains standard instructions and warnings about communications and payment, along with a unique victim identifier. It also has the standard warnings against not working with them.
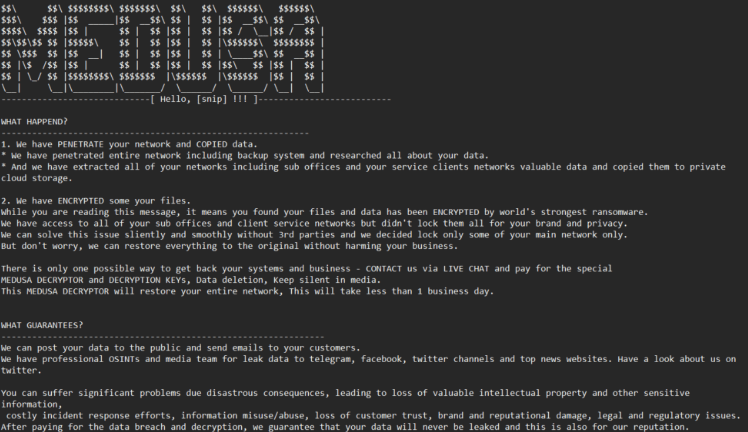
Partial Medusa ransom note. See the full note at Ransomware.Live
Defend yourself
Almost all advanced threats rely on an individual’s mistakes. Here are some best practices for each person to follow:
- Use strong, unique passwords for all accounts and enable multi-factor authentication (MFA) wherever possible. This adds an extra layer of security by ensuring that even if attackers steal your credentials, they cannot easily access your accounts without the additional authentication factor.
- Update your operating system, applications, and antivirus software on your personal devices regularly. Malware infects many devices, stealing credentials and other information. Cybercriminals mine this stolen data for use in credential stuffing and other initial access attacks.
- Avoid clicking on suspicious links or downloading attachments from unknown sources. Accidentally running a malicious file can install information stealers and other malware that could damage your device and spread to other devices on your home network.
Protecting your company requires these best practices and a lot more:
- Update all operating systems, applications, and firmware to the latest versions to patch vulnerabilities that ransomware exploits. Plan early for Windows 10 end of support (October 14, 2025).
- Use a robust backup solution that offers immutable backups that cannot be altered by ransomware. Replicate and store at least one copy of the backups off the network.
- Apply the principle of least privilege by limiting administrative access to only those who absolutely need it. Use role-based access controls to minimize exposure. Disable unused remote access tools or secure them with strong passwords and MFA.
- Use AI-powered endpoint protection to monitor for suspicious activity and respond to attacks. Barracuda Managed XDR offers advanced threat intelligence and automated incident response that will identify and mitigate attacks while the company teams work on recovery.
- Create a detailed incident response plan that includes isolating infected systems, communicating securely during an attack, and restoring operations from backups. Test this plan regularly and address any gaps.
- Deploy a strong, AI-powered email protection system that includes SPF, DMARC, and DKIM protocols. Conduct regular training programs to teach employees how to recognize phishing emails, avoid suspicious links, and report potential threats immediately.
- Use network segmentation to isolate critical systems and data from less secure areas. This will slow down and possibly prevent lateral movement throughout the network, which is what a threat actor needs to execute the full attack chain. Medusa will prioritize sensitive data for exfiltration, so make it difficult and time-consuming for them to find.
- Require MFA for all accounts and systems company-wide. This basic procedure adds an extra layer of security against unauthorized access.
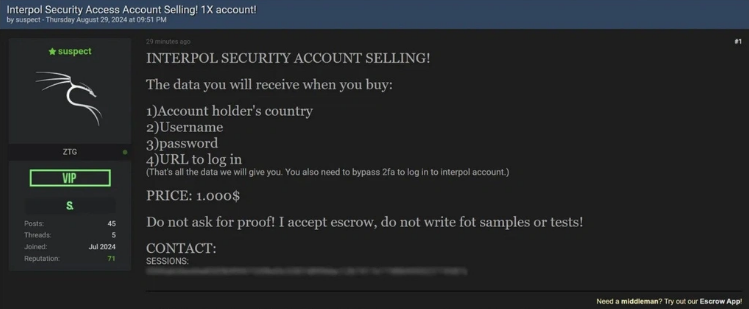
Threat actor selling Interpol credentials, warning of two-factor authentication
Barracuda can help
Barracuda provides a comprehensive cybersecurity platform that defends organizations from all major attack vectors that are present in today’s complex threats. Discover the best value with feature-rich, one-stop solutions from Barracuda that protect against a wide range of threat vectors, all backed by complete, award-winning customer service. Because you are working with one vendor, you benefit from reduced complexity, increased effectiveness, and lower total cost of ownership. Over 200,000 customers worldwide count on Barracuda to protect their email, networks, applications, and data.
This article was originally published at Barracuda Blog.
Photo: feriagashi / Shutterstock

