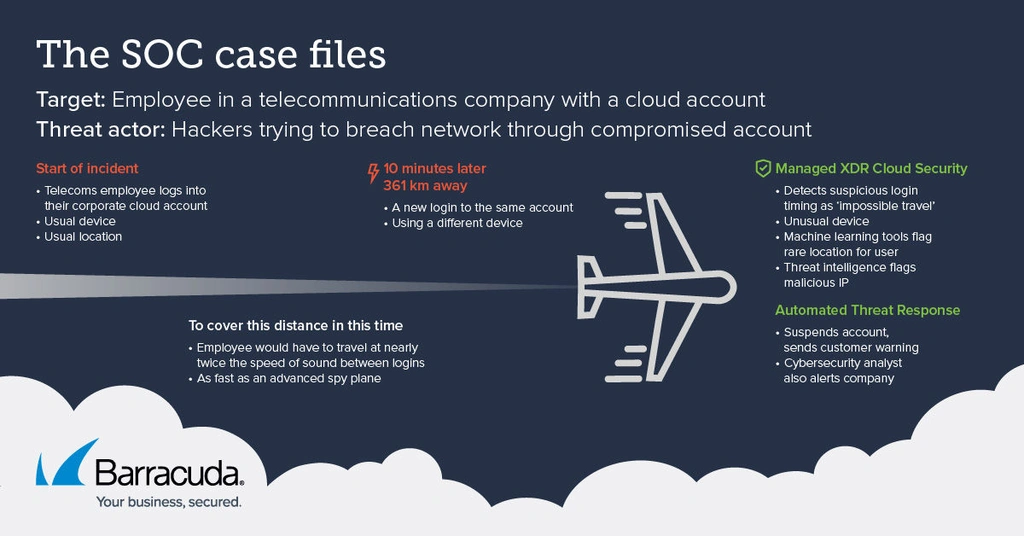
- An employee at a telecommunications company connected as usual to their cloud account.
- They then appeared to travel a distance of 361 km, roughly 225 miles, at nearly twice the speed of sound before logging in again, according to the data reaching Barracuda Managed XDR’s automated detection systems.
- These detection systems simultaneously registered that:
- The second user login used a different device.
- The second login came from an IP and location that was unusual for this user.
- The system flagged this IP as malicious.
- Taken together, the data showed a 99% chance that a threat actor had compromised the account.
- Since the company had Automated Threat Response as part of XDR Cloud Security, the system automatically suspended the impacted account, alerted the customer, and shut down the incident.
The incident was detected, contained, and mitigated by the Automated Threat Response functionality of Barracuda Managed XDR Cloud Security. Barracuda Managed XDR is an extended visibility, detection, and response (XDR) service that provides customers with round-the-clock human and AI-led threat detection, analysis, incident response, and mitigation services to protect against complex threats.
How the attack unfolded
One afternoon at around 3:25 p.m., an employee at a telecommunications company connected to their cloud account with their usual device and from their usual location.
- They then appeared to travel at over 2,160 km per hour, the speed of an advanced Lockheed SR-71 Blackbird reconnaissance plane, to a location they’d rarely visited, if at all, and logged into their account again using another device.
- This anomalous activity triggered a whole range of red flags in Barracuda XDR detection systems.
- The system identified the second login as suspicious and unauthorized.
- It exhibited four characteristics that suggested account compromise with 99% confidence:
- The ‘impossible travel’ scenario, a distance of 361 km (roughly 225 miles) traveling at nearly twice the speed of sound between logins.
- The attacker used a different device in the second, suspicious login.
- Barracuda Managed XDR’s machine learning indicators flagged the IP address and location associated with the suspicious login as ‘rare’ for the impacted user account.
- Threat intelligence flagged the IP address used in the suspicious login event as possibly malicious.
Threat response and mitigation
- Not long after the second login attempt, XDR’s machine-learning model validated the anomalous characteristics of the suspicious login event and triggered a malicious detection alert.
- Six minutes later, XDR automatically suspended the impacted account and issued a security warning to the organization.
- A cybersecurity analyst from the SOC followed up with a call to the organization to let them know in person. The organization confirmed the incident as a true positive.
Key learnings
- Organizations can enhance their protection against such incidents by implementing security solutions like Barracuda Managed XDR with Automated Threat Response and advanced, multilayered email protection. Additionally, they can harden security through robust policies and employee training.
- This should include conditional access policies — such as only allowing authentication from authorized locations — multifactor authentication measures (MFA), and rotating credentials regularly to avoid having stale/leaked passwords in active use.
- Security awareness training will help to prevent users from falling victim to MFA fatigue and increasingly complex and evasive phishing attacks.
Barracuda Managed XDR features like threat intelligence, Automated Threat Response, and the integration of wider solutions such as XDR Server Security, XDR Network Security, and XDR Cloud Security, provide comprehensive protection and can drastically reduce dwell time.
For further information on how Barracuda Managed XDR and Security Operations Center can help you, please contact us.
This article was originally published at Barracuda Blog.
Photo: Jag_cz / Shutterstock




People are still going to make mistakes, so this type of layered security ‘automation’ will be paramount to further advance protections against account compromises. Impossible travel seems like a ‘gimme’, though, as the threat actors have gotten far more sophisticated in setting up local domains to trick the algorithms. How can we further advance detection to detect anomalies that are most likely threats while not disrupting end user productivity?
Barracuda Managed XDR with Automated Threat Response and advanced features is an excellent choice for reducing human intervention when responding to incidents. The only challenge it may face is false positives, which could impact employee performance.
This article does a great job explaining how XDR and automation can make cloud security faster and more effective. I really liked the real-world examples from SOC teams—it makes the topic feel practical and relevant. It’s a helpful read for anyone looking to understand how technology is shaping modern cybersecurity.
Another swell read. More companies should be aware they need this time of additional security layer.
Barracuda Managed XDR with Automated Threat Response is a fantastic layer of security, for all the mistakes we Humans make.