
 1-in-5 cyberthreats detected between June and the end of September 2022 were higher risk, compared to just 1-in-80 in January.
1-in-5 cyberthreats detected between June and the end of September 2022 were higher risk, compared to just 1-in-80 in January.
XDR data shows that between June and September, the top threats were successful Microsoft 365 logins from a suspicious country (accounting for 40% of attacks), followed by communication from the network to a known dangerous IP address (15% of attacks), and brute force user authentication attempts (10%).
Introduction
The volume, nature, and intensity of cyberthreats targeting organizations varies over time, reflecting evolving attacker behaviors as well as improving security methodologies and intelligence fine-tuning — and more. Understanding these trends can help organizations to better anticipate attacks and prepare their defenses.
The latest threat insight from Barracuda’s advanced XDR platform and 24/7 Security Operations Centre looks at what happened to threat volume and severity during 2022 — with a special focus on the summer months.
The data is drawn from the customers and MSP partners that rely on Barracuda XDR to detect, analyze, and respond to suspicious or malicious threats.
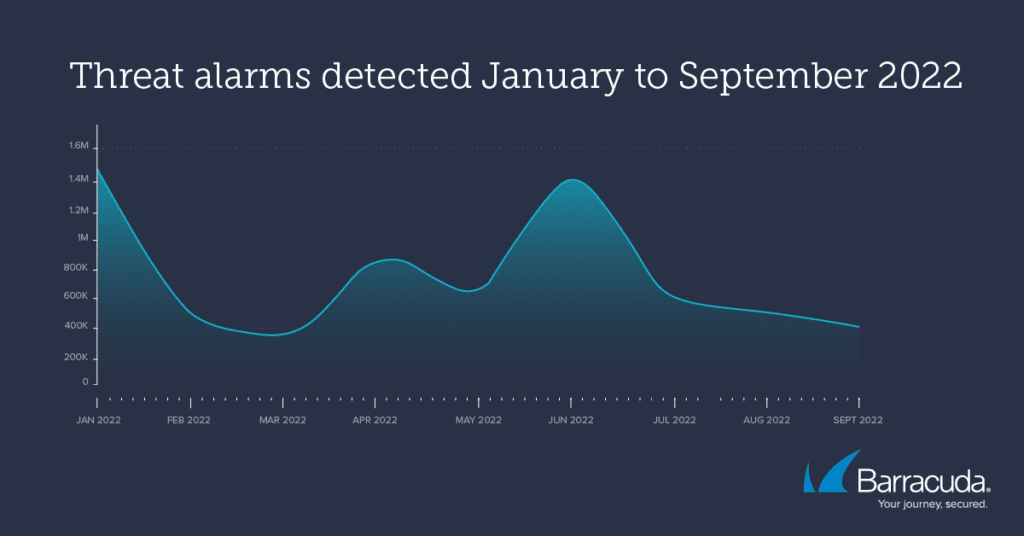
From alarms to customer warnings
The picture is very different when you look at how many of those threat alarms triggered a customer security alert once Barracuda’s threat experts had taken a closer look.
In January, only around 1.25% of threat alarms or 1-in-80 (17,500) were serious enough to warrant a security alert to the customer — but fast forward to June to September and the rate goes up to 1-in-5 (96,428).
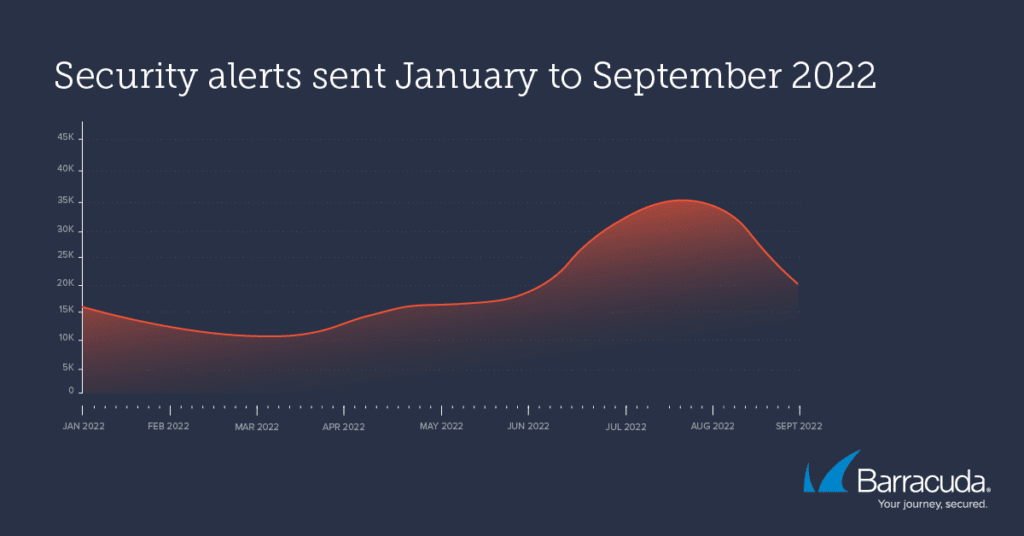
A closer look at the summer threat alerts
Of the 476,994 threat alarms analyzed by Barracuda threat experts between June and September, 96,428 or 20% were sufficiently serious for the customer to be alerted to the potential danger and urged to take remedial action.
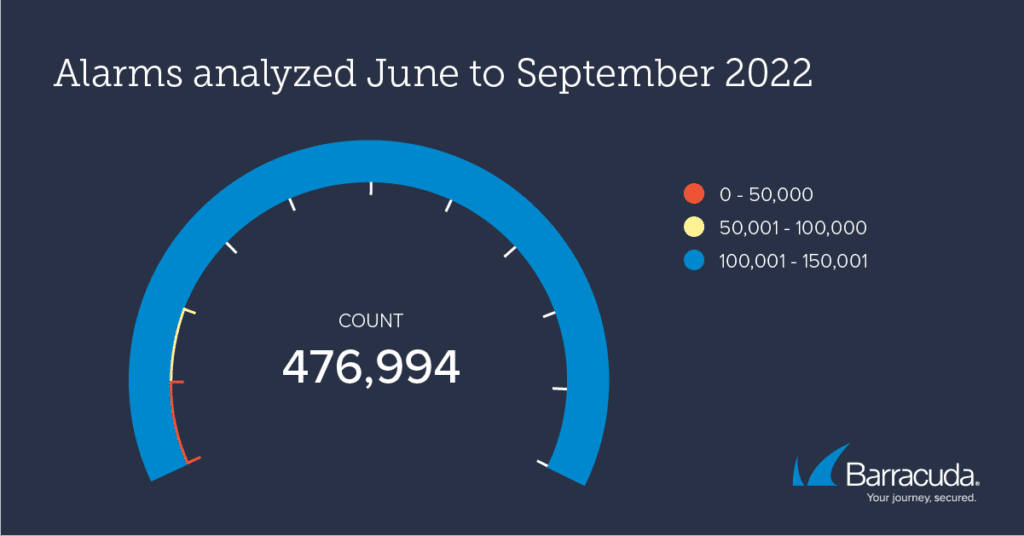
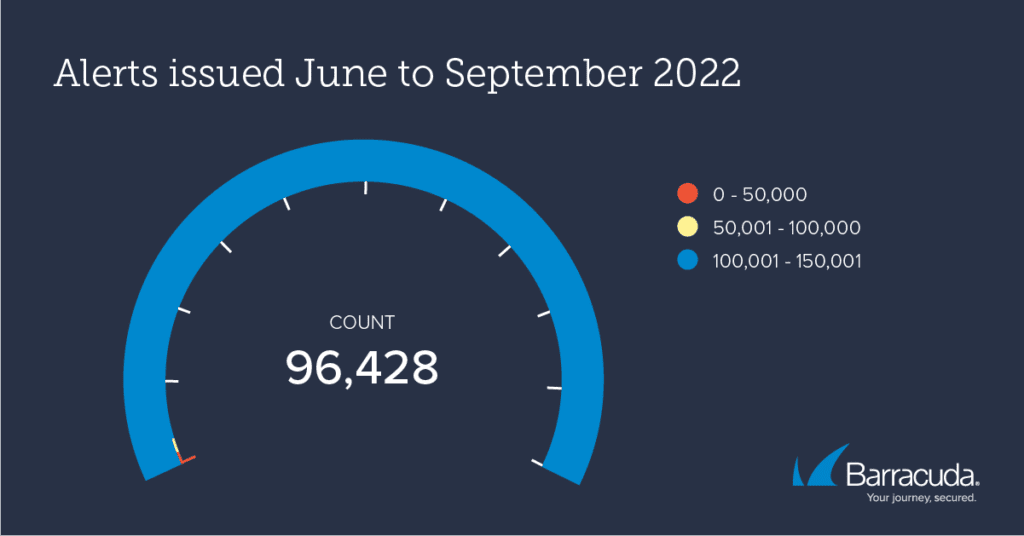
The three most frequently detected threats between June and September were as follows:
1. Successful Microsoft 365 login from a suspicious country — classed as “high risk”
This type of attack accounted for 40% of all attacks during the 90-day window between June and the end of September. The countries that flag an automatic security alert include Russia, China, Iran, and Nigeria. A successful breach of a Microsoft 365 account is particularly risky because it offers an intruder potential access to all the connected and integrated assets the target has stored on the platform. Among other things, analysts look for evidence of multiple-country logins to the same account, such as one from the UK followed an hour later by one from Russia or China. Just 5% of these alarms were “false positive” legitimate logins.
“High risk” threats are actionable events that have the potential to cause severe damage to customer environment and which demand immediate action.
2. Communication to an IP address known to Threat Intelligence – “medium risk”
This type of attack, accounting for 15% of all attacks during this period, includes any attempt at malicious communication from a device within the network to a website or known command-and-control server, etc.
“Medium risk” require mitigation but wouldn’t typically lead to substantial impact as a standalone event.
3. Brute force authentication user attempt — “Medium Risk”
Accounting for 10% of all attacks, these are automated attacks trying to penetrate an organization’s defenses by simply running as many name/password combinations as they can.
What does the data mean?
Cyberattackers target companies and IT security teams when they are likely to be under-resourced. This could be on weekends, overnight, or during a holiday season, such as the summer.
This is reflected in the XDR data, which clearly shows that despite an overall reduction in threat volume, a significantly greater proportion of threats detected during the summer months were at the higher-risk end of the scale.
This is worth bearing in mind as we head into another holiday season.
Barracuda recommends that IT security teams reinforce essential security measures, such as:
- Enabling multifactor authentication (MFA) across all applications and systems
- Ensuring all critical systems are backed up
- Implementing a robust security solution that includes email protection and Endpoint Detection and Response (EDR)
- Visibility across the whole IT Infrastructure
- A round-the-clock (24×7) Security Operations Center (SOC) to monitor, detect, and respond to cyberthreats — either in-house or via a trusted service provider.
The findings are based on detection data from Barracuda XDR, an extended visibility, detection, and response (XDR) platform, backed by a 24×7 Security Operations Center (SOC) that provides customers with round-the-clock human and AI-led threat detection, analysis, incident response, and mitigation services. For more information, visit our website.

Love this meaningful data that can be shared with customers and prospects to emphasize the need for cyber vigilance ALL of the time.
Can’t IT staff just take some time off and not need to worry about this 24 x 7?
Great article
As we head into this busy time of year, it is important to remember that the bad guys never rest
Very insightful article. Interesting to see the trends for that period.
Great data, and a good reminder that we all need to be more prudent with these threats during the summer months.
great info, and reminder that everyone will busy ramping up to for the holidays and not to let things slide.