 Security has always seemed to be at the top of most organizations’ mind. At the same time, it is often a lower priority when setting aside discrete investment. Outsourcing functions to an MSP can be seen by many as a way of outsourcing security, too – but just what is expected to be included in a base price and what can be leveraged to increase a price while not significantly impacting costs?
Security has always seemed to be at the top of most organizations’ mind. At the same time, it is often a lower priority when setting aside discrete investment. Outsourcing functions to an MSP can be seen by many as a way of outsourcing security, too – but just what is expected to be included in a base price and what can be leveraged to increase a price while not significantly impacting costs?
 Platform security must be solid
Platform security must be solid
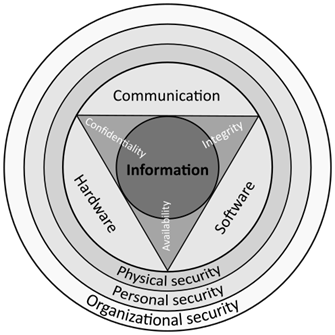
At the most basic level, platform security (hardware, software, communication) must be taken as table stakes. No prospect is going to pay extra just because an MSP states that it can prevent malicious actors from penetrating the platform and stealing data or bringing the entire environment down. However, the counter point to this is that if your platform does suffer such a breach, then it could very well be game over unless you can demonstrate that this was a novel attack that could have impacted any other similar platform.
At the physical security level, there is a degree of room for positive messaging. Although the majority of MSPs will have measures in place to ensure that their platform is physically secure, not all prospects are aware of what this can entail. Ensuring that ram-raiding of a physical location is prevented using bollards or large planters is a starting point. Ensuring that any room with access terminals in it does not have external-facing windows where malicious actors can either use long-range zoom cameras to capture data or vibration sensors to capture voice, starts to move things up a notch.
Partitioning access and centralized monitoring can narrow attack surfaces
Rules around who is allowed into the building at all, what areas they are allowed to access, and what activities they can carry out starts to create a physically solid environment. Ensure that personnel systems are tied into to the MSP’s and customers’ help desk systems so that trouble tickets are used as a means of both ensuring that everybody understands what the problem is and who is going to try and rectify it further narrows down areas for malicious attacks.
Where third parties are involved, such as engineers from suppliers of OEMs coming in to repair equipment, ensure that everything is fully logged and that the supplier/OEM names who will be coming.
Wherever possible, section off parts of the platform depending on the required security levels. For example, customers who require (and pay for) higher levels of security should have either shared or dedicated equipment held in cages so that they are separated away from any other personnel in the datacenter. Those with the highest levels of security requirement may have dedicated systems placed in blanked-off cages – and the cages may run from solid ceiling to solid floor, rather than dropped ceiling to raised floor.
All of these provide levels of differentiation that can be sold as added value to prospects – with relatively low outlay from the MSP.
Adherence to security standards can differentiates MSPs
A relatively simple way for MSPs to show how serious they take security, is to adhere to the agreed global security standards. The most known of these is the family of ISO standards under ISO/IEC 27000. ISO/IEC 27001:2022 specifies a management system that provides information security, cybersecurity, and privacy protection. ISO/IEC 27002 provides a high-level guide to cybersecurity and gives the reader details as to what is required to gain ISO/IEC 27001:2022 accreditation.
ISO/IEC 21827 defines what is known as the ‘Common Criteria’. This enables mixed equipment to be tested and certified against common levels of security as a complete platform.
Bringing in national, regional, and vertical-specific security standards will also allow MSPs to differentiate themselves in the market.
However, personnel must be capable of supporting such standards – look to employ and maintain the skills of employees in suitable security areas, such as CompTIA Security+ (SYO-601), Certified Information Systems Security Professional (CISSP), ISACA Certified Information Security Manager (CISM) or (ISC)² Certified Cloud Security Professional (CCSP). These can then be leveraged along with the various ISO/IEC standards to demonstrate that an MSP is truly taking security seriously.
With information security, again look to adherence to accepted global, regional, and national requirements, such as the EU’s General Data Protection Regulation (GDPR), with data being held regionally and not being moved beyond restricted borders. Also look to the use of VPNs and data encryption on the move and at rest to further secure information.
This then opens further possible revenue streams for MSPs, using regional information stores with secure enterprise workflow solutions, data leak prevention (DLP), and digital rights management (DRM) being used to centrally control how information is used and actions that can be taken upon it.
Finally, through working with the customer or prospect, data analysis can be used to gather insights into what is happening, and advice provided to enhance personal and organizational security to better meet a customer’s information security needs.
MSPs must communicate value
Overall, security still struggles to light up a conversation with a prospect as to why they should use an MSP. However, the idea is to point out what advanced security means to them on a risk and reward basis when they are dealing with their own suppliers and customers – and show that the MSP can provide them with far better capabilities than the customer could possibly do on their own – at a reasonable additional cost.
Photo: Song_about_summer / Shutterstock
 Platform security must be solid
Platform security must be solid