Most Discussed Posts

Cybersecurity predictions for 2021
Last year, the COVID-19 pandemic pretty much dominated everything, which created many challenges for MSPs. What does 2021 hold in the realm of cybersecurity? Unfortunately, perhaps more of the same, according to Hussain Aldawood, Director of Cybersecurity, for Saudi Arabia-based...
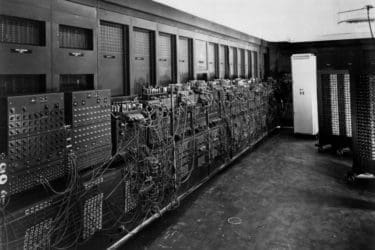
Pioneers in Tech: The ENIAC Six
On Feb. 14, 1946, John Mauchly and J. Presper Eckert unveiled one of the U.S. Army’s best-kept secrets of World War II: the ENIAC. The Electronic Numerical Integrator and Computer was built behind closed doors in a restricted area at...

New AWS services optimize application development process
Amazon Web Services (AWS) consistently introduces new services, enhances existing ones, and drives trends that all contain technology, capabilities, and information of great relevance to MSPs. In the first half of 2020, AWS announced a significant number of developments that...

Organizations need WFH help from MSPs now more than ever
Many organizations are just now starting to come to terms with the inherent challenges with supporting employees as an anticipated second wave of COVID-19 infections appears to be all but inevitable. A survey of more than 100 C-level executives and...

Managing by the numbers: 3 KPIs for your MSP sales process
Are you trying to decide whether or not you would like to engage with a sales and marketing vendor? Are you considering hiring a telemarketer, hiring a social media manager or hiring a sales rep? Maybe you are trying to...

Unified communications: pointers for a permanent remote workforce
As COVID-19 stay-at-home orders are gradually lifted and states begin to return to some semblance of everyday life, we shouldn’t assume an automatic return to the office. Businesses across the globe have learned during the pandemic that their workforce is...

Ask an MSP Expert: Should I monitor my employees?
Q: Due to the pandemic, my MSP’s employees are now working remotely. I don’t like the idea of “spying” on my employees, but I also miss being able to pop my head in someone’s office to chat and check on work....

Salesforce Research: Workers see a hybrid work/office future
Employees are starting to return to the office, either partially or fully depending on their unique situations, and as an MSP you might be seeing that happen with your customers. This begs the question what will going back to the...

Your MSP isn’t all about price
As someone who spends a lot of time talking and writing about how managed services providers (MSPs) need to make their messaging all about the raw value they’re able to offer their prospects, I hear a lot of people say...

Tech Time Warp: A Technological Whirlwind at MIT
July 4, 1956, doesn’t quite rank with July 4, 1776, in terms of independence, but it was a remarkable day in terms of freedom for computer users—freedom from punch cards, dials, and switches, that is. On July 4, 1956, researchers...
